Container Registry
Introduction
Container Registry is a service for storing private container images. It provides a subset of features offered by Artifact Registry, a universal repository manager and the recommended service for managing container images and other artifacts.
Artifact
Artifact Registry extends the capabilities of Container Registry. In addition to supporting multiple artifact formats, the service provides additional benefits such as the ability to create multiple discrete repositories in the same region.
Working with Your Images
Many people use Docker Hub as a central registry for storing public Docker images, but to control access to your images, you need to use a private registry such as Container Registry.
You can access the registry through secure HTTPS endpoints, which allow you to push, pull, and manage images from any system.
Getting Started
How to Launch Container Registry from My Account Portal
Login into My Account
Please go to ‘My Account’ and log in using your credentials set up at the time of creating and activating the E2E Networks ‘My Account’.
Navigate to Container Registry Create Page
- Go to ‘My Account’ and log in using your credentials.
- After logging in, on the left side of the My Account dashboard, click on the “Container Registry” sub-menu available under the Storage section.
- You will be directed to the ‘Container Registry manager’ page.
Working with Container Registry
The following sections describe how you can use Container Registry.
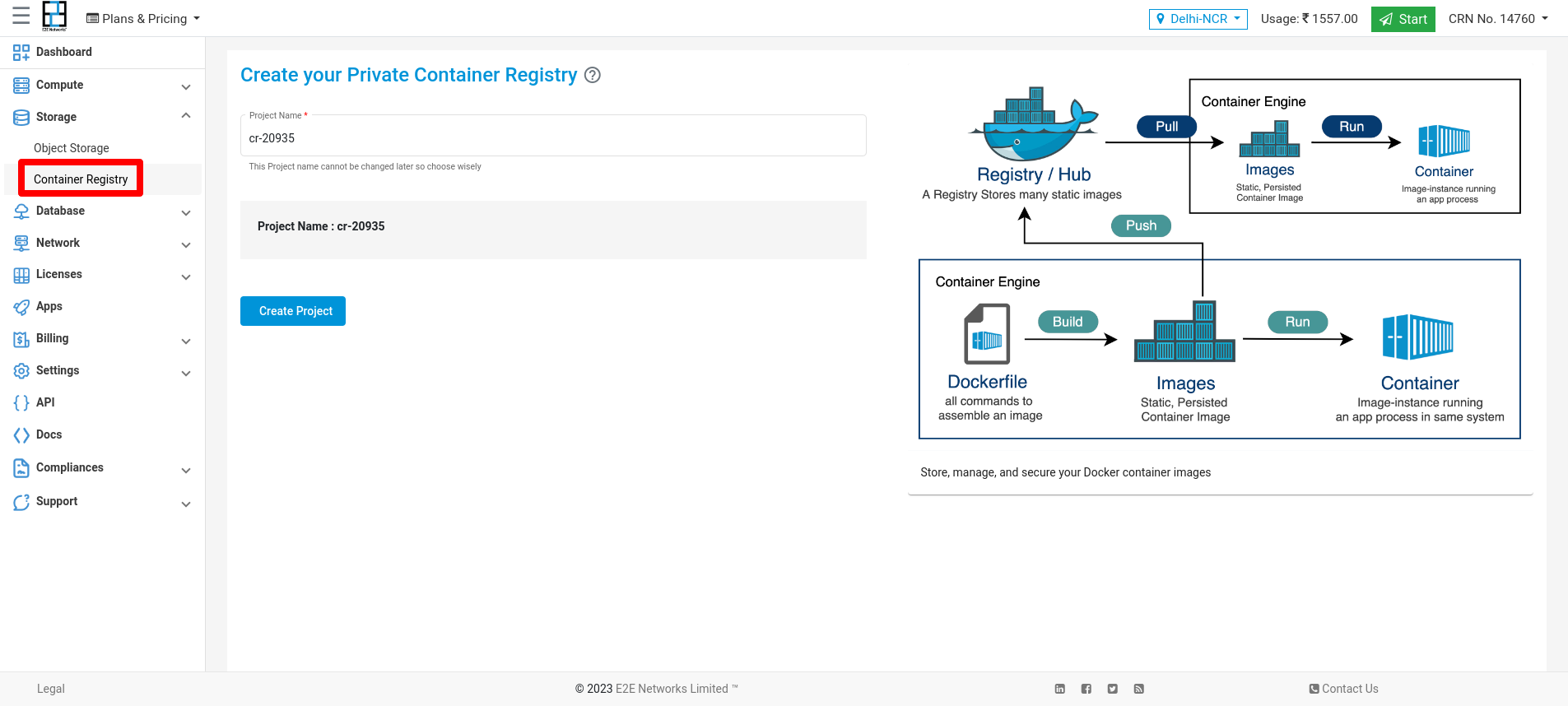
Create New Container Registry
- Click on the "Container Registry” sub-menu available under the Storage section.
- You will be directed to the ‘Container Registry manager’ page.
- You can provide the project name (optional).
- Click on the “Create Container Registry” button.
Actions
You can perform the following actions available for the respective container registry:
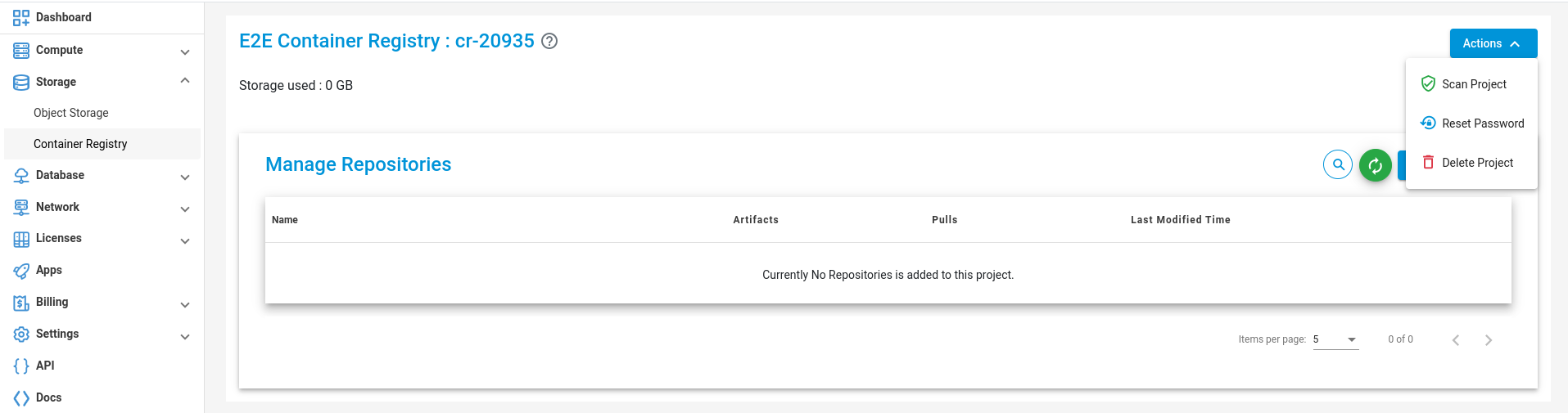
Scan Project
Click on the scan Project button to scan your Project.
Reset Password
Click on the Reset Password button to change the password of your Project.
Delete Project
Click on the Delete Project button to delete your Project.
Connecting to Your Container Registry
Enter the following command at a command prompt on your local or client desktop to connect to a container Registry.
docker login registry.e2enetworks.net -u <user_name> -p <password>
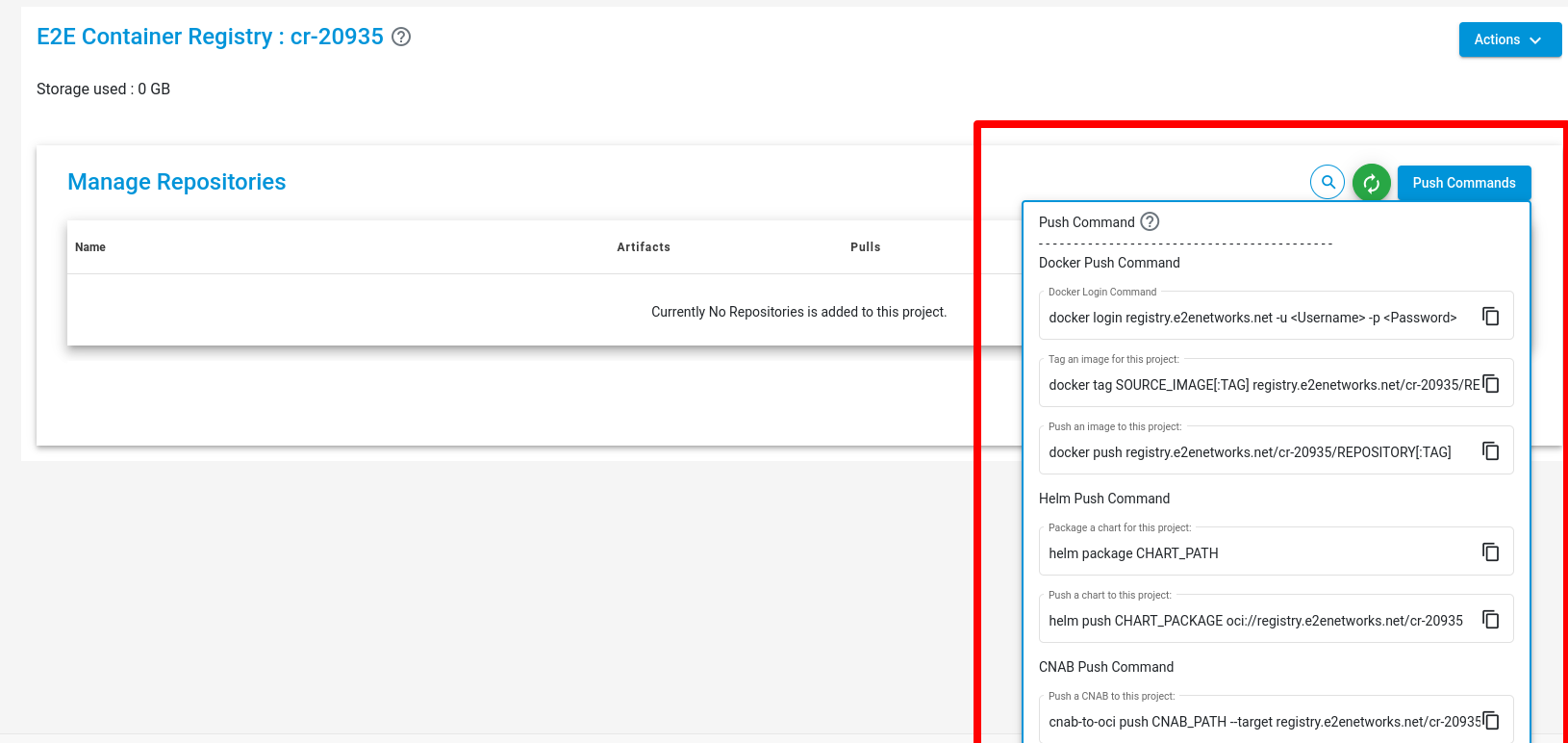
Push Command
Using Docker
Enter the following command to push your image on the project.
Create tag -
docker tag <image> registry.e2enetworks.net/<project_name>/<image>
Push Image -
docker push registry.e2enetworks.net/<project_name>/<image_name>
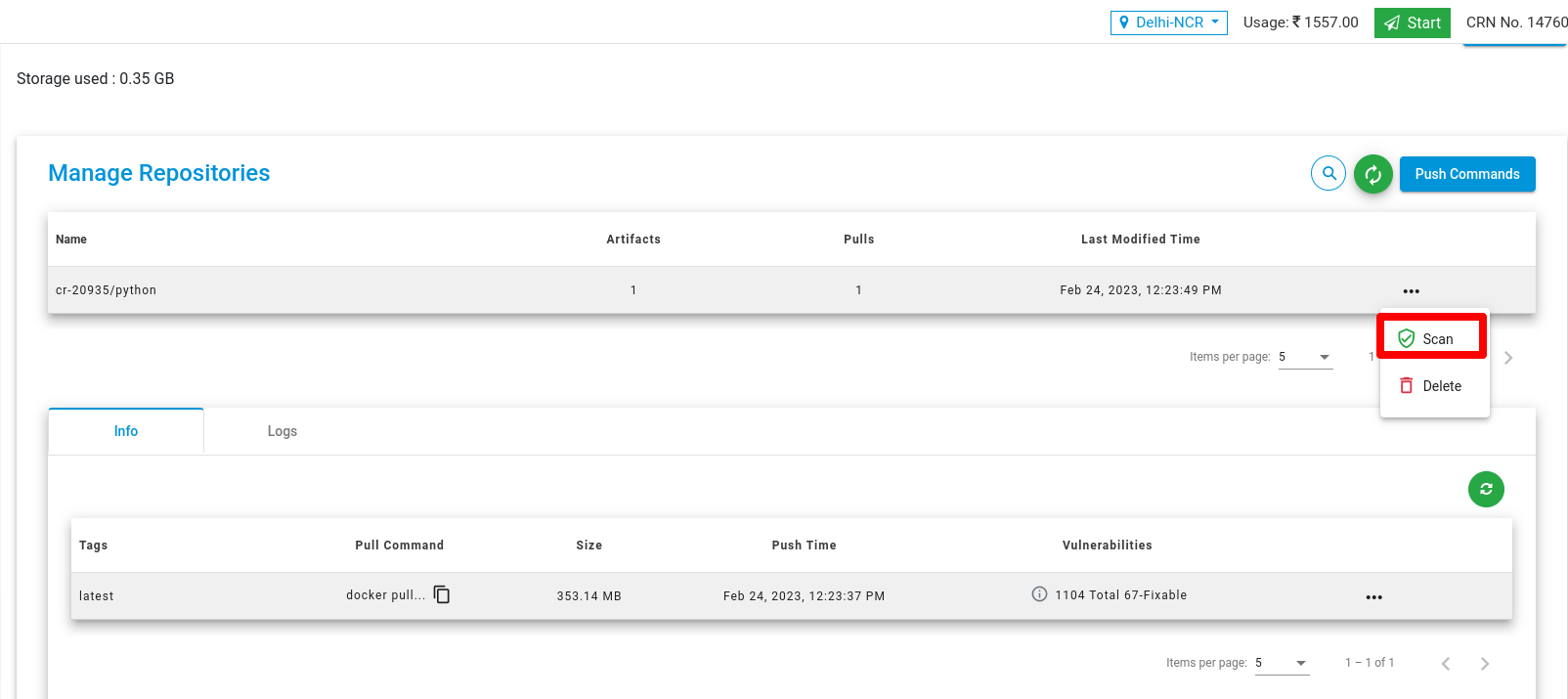
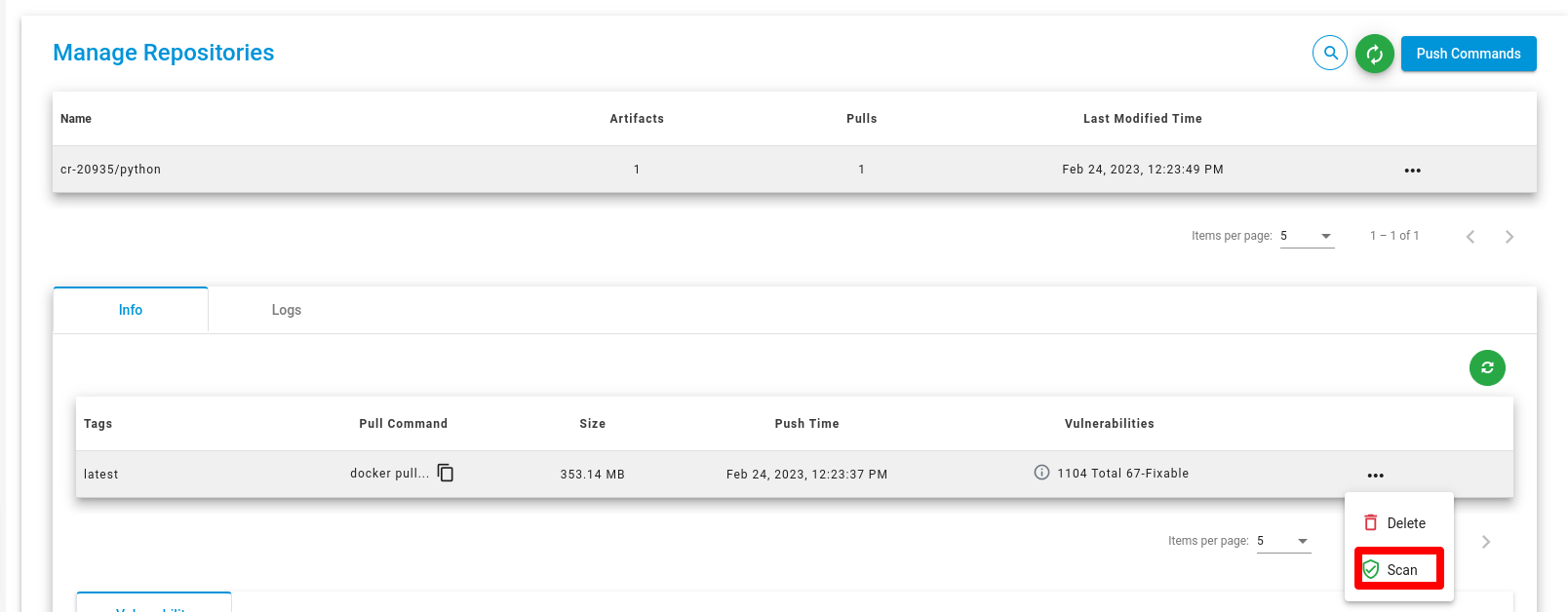
Scan Repositories
To scan repositories, click on the scan button to scan your repositories.
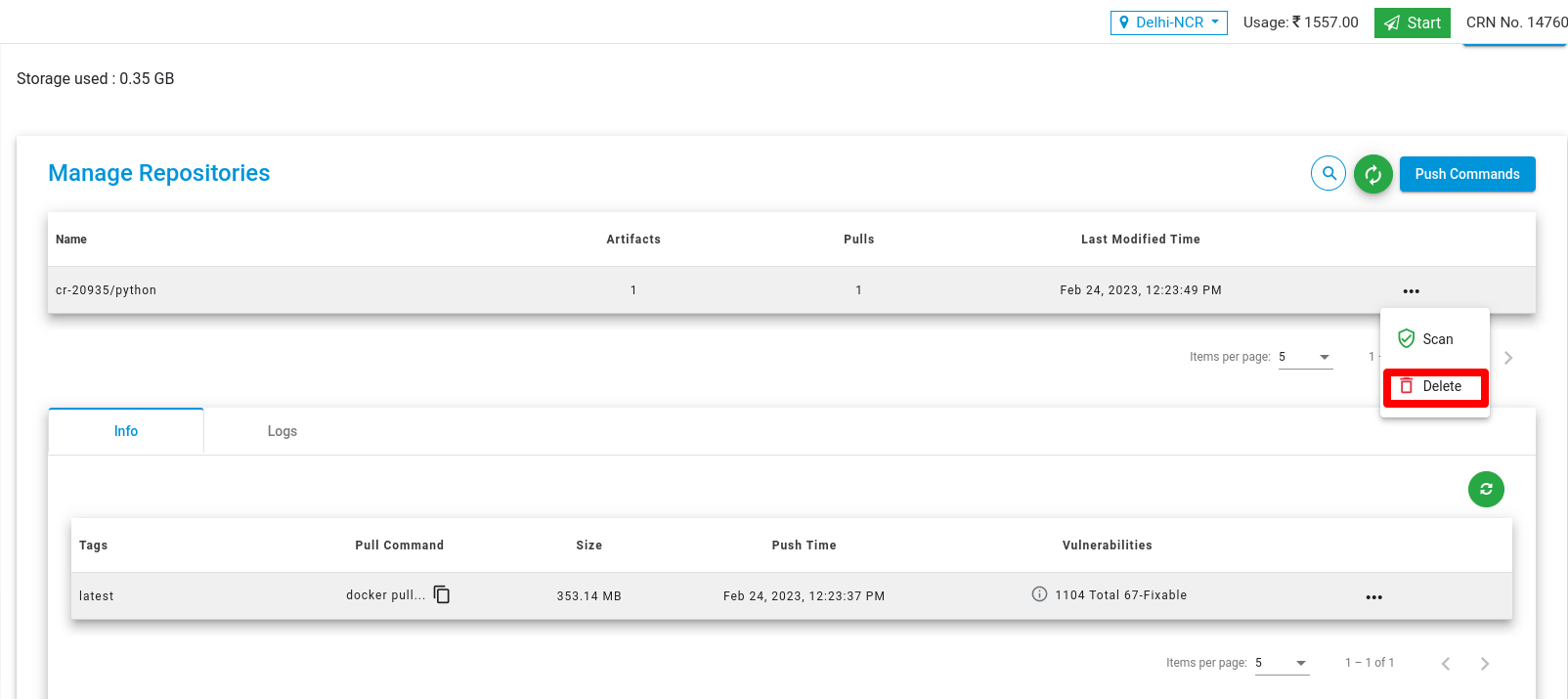
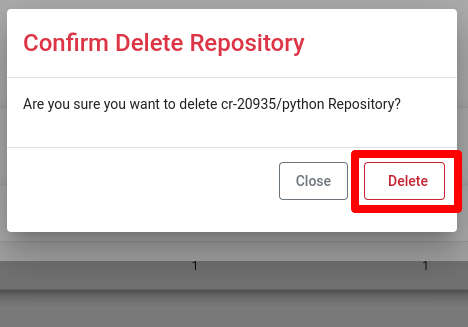
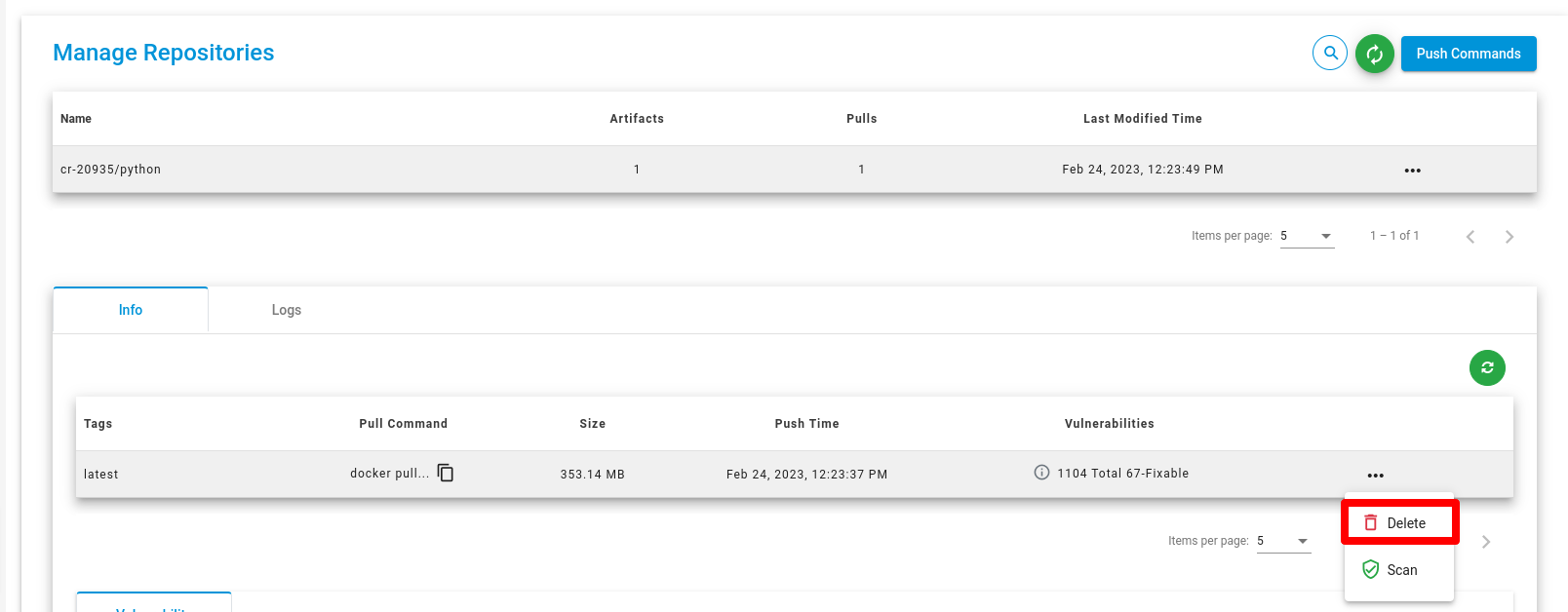
Delete Repositories
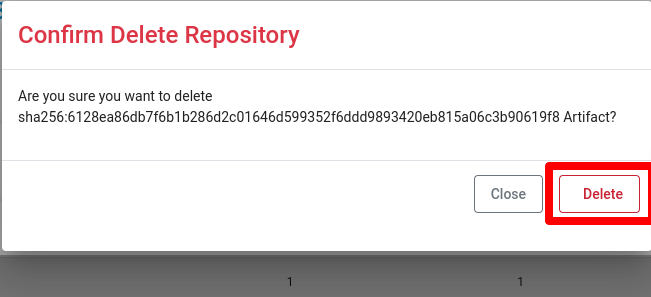
To delete a repository, click on the Delete button. A confirmation popup will appear, and you need to confirm by clicking the Delete button.
Scan Artifact
To scan the artifact, click on the scan button for the artifact.
Vulnerability
A vulnerability scan in a container registry is a security process that involves examining container images stored in the registry for known vulnerabilities. These vulnerabilities could be related to software dependencies, libraries, or other components within the container image that might have security flaws.
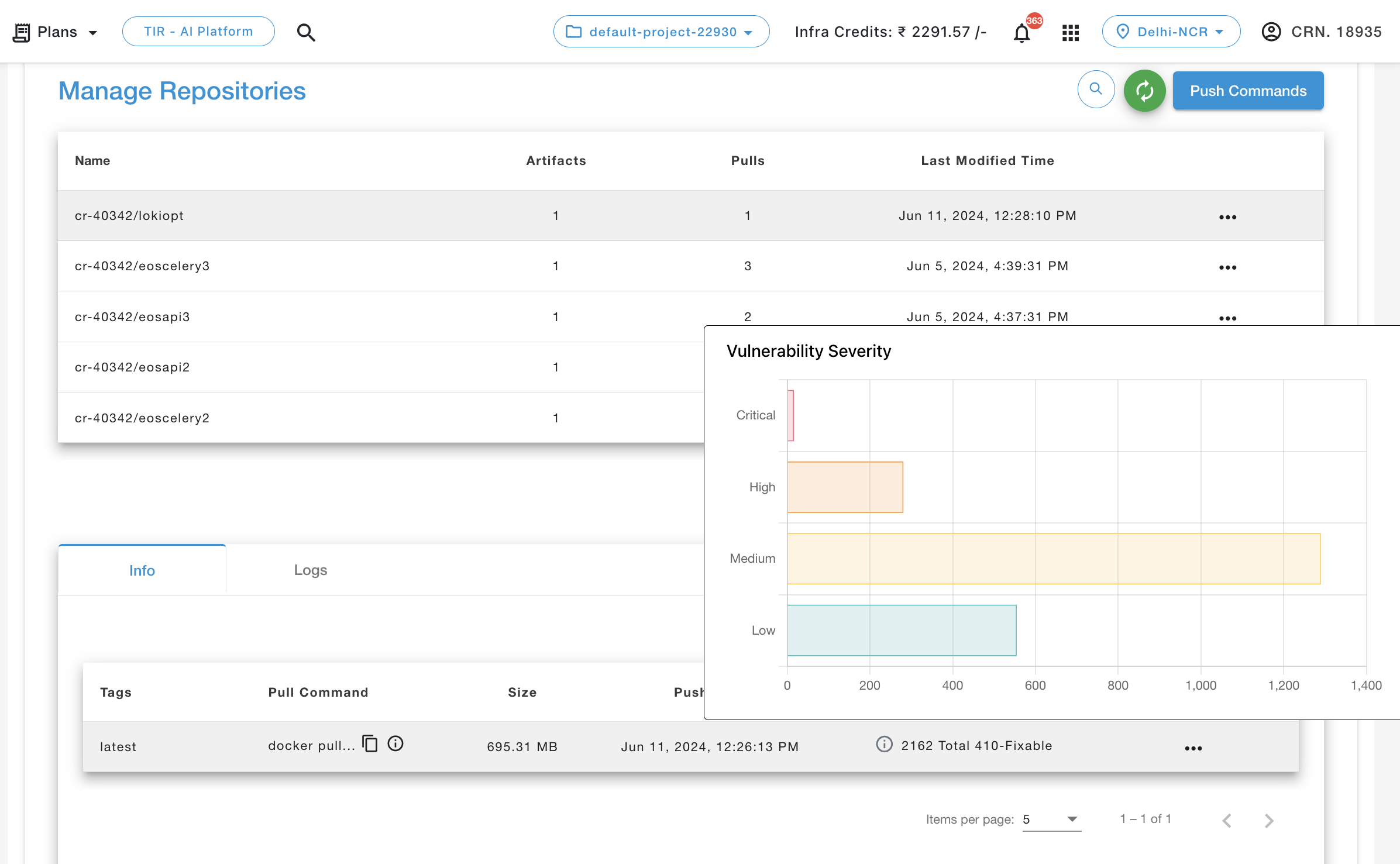
In the above screenshot:
- Red: At least one critical vulnerability found
- Orange: At least one high-level vulnerability found
- Yellow: At least one medium-level vulnerability found
- Blue: At least one low-level vulnerability found
- Green: No vulnerabilities found
- Grey: Unknown vulnerabilities
In the vulnerabilities section, it shows a list of vulnerabilities and their respective details.
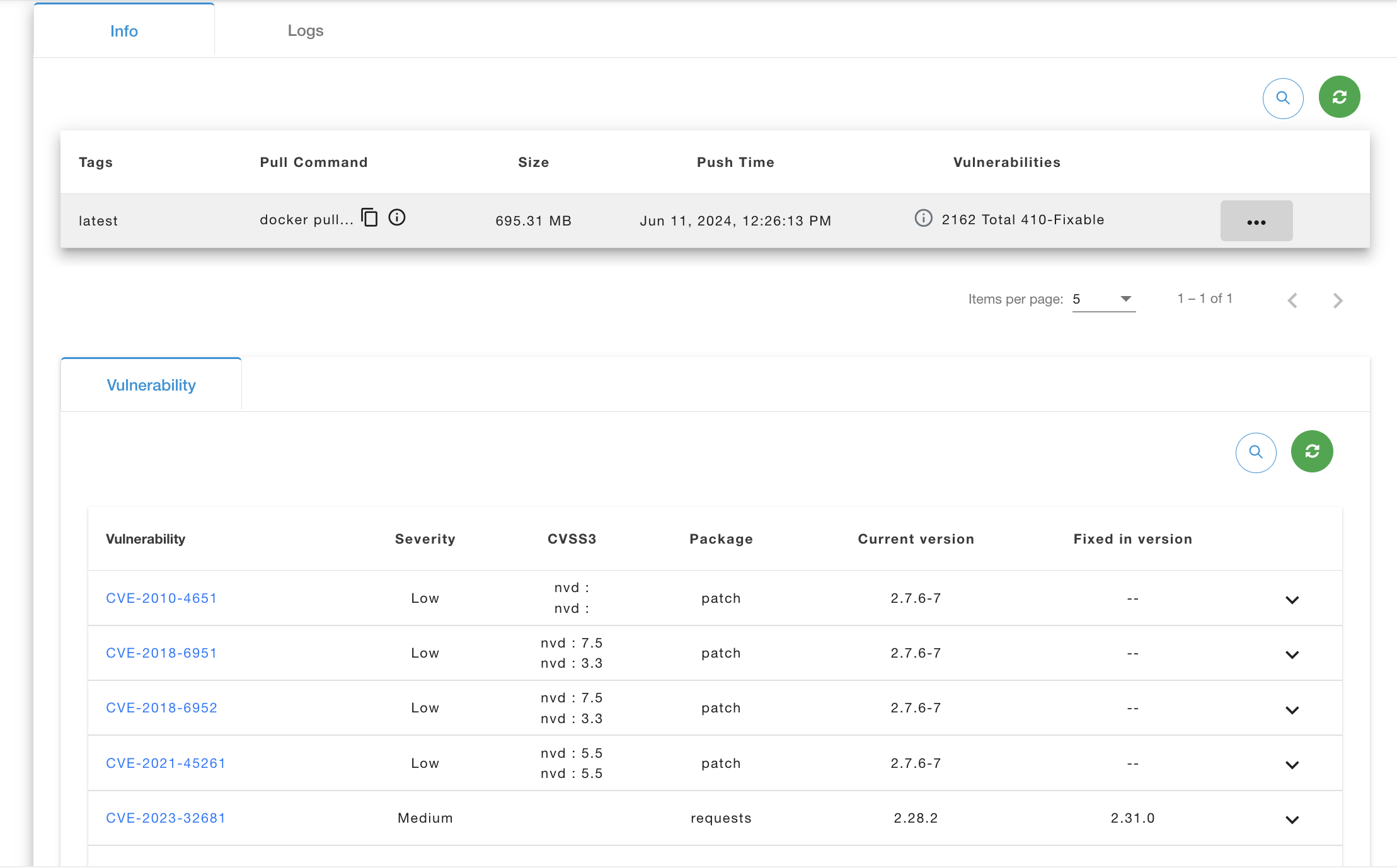
Delete Artifact
Click on the Delete button to delete your artifact. A confirmation popup will open, and you need to confirm by clicking the Delete button.
Connecting Kubernetes to Container Registry
Secrets
A Secret is an object that contains a small amount of sensitive data such as a password, a token, or a key. Such information might otherwise be included in a Pod specification or in a container image. Using a Secret means that you don't need to include confidential data in your application code.
Create Secrets
kubectl create secret docker-registry name-secrets \
--docker-username=username \
--docker-password=pass1234 \
--docker-server=registry.e2enetworks.net
cat > private-reg-pod-example.yaml << EOF
apiVersion: v1
kind: Pod
metadata:
name: node-hello
spec:
containers:
- name: node-hello-container
image:registry.e2enetworks.net/vipin-repo/node-hello@sha256:bd333665069e66b11dbb76444ac114a1e0a65ace459684a5616c0429aa4bf519
imagePullSecrets:
- name: name-secrets
EOF