How To Set-Up SSH Keys – Linux
Introduction
Setting up SSH based security to access your server is a much more effective way than the use of a manual root password. Cracking the security system of a node depending on SSH keys is nearly impossible since it secures your node in a more sophisticated way by the use of encoded keys.
Why is a password-based authentication vulnerable?
A server can authenticate & grant access to the users with different access methods. The most basic of these is a password-based authentication, which is easy to use but isn’t the most secure.
Modern processing power combined with automated scripts make brute forcing a password-protected account very possible since passwords generally are not complex. SSH keys prove to be a reliable and secure alternative.
What are SSH Keys?
SSH key pairs are two cryptographically secure keys that can be used to authenticate a client to an SSH server. Each key pair consists of a public key and a private key.
The private key is retained by the client on his local machine and should be kept absolutely secret. Any compromise of the private key will allow the attacker to log into servers that are configured with the associated public key without additional authentication. As an additional precaution, the key can be encrypted on disk with a passphrase.
The public key is uploaded onto the remote server that you want to be able to log into with SSH. When a client attempts to authenticate using SSH keys, the server can test the client on whether they are in possession of the private key. If the key-pair matches then a shell session is spawned or the requested command is executed.
How do SSH keys work
A key pair will be generated on your local PC.
Generating a key pair provides you with two long string of characters: a public and a private key.
The public key will be added to your node.
The corresponding private key pair will be saved on your local PC.
Every time you access your node, the SSH system will look up for the private key pair of the public key added to it. The system will unlock only when the two keys match.
You can also disable the root password after the SSH keys are set up.
Setup SSH Keys – Linux
Follow the below given steps to set up SSH keys:
Step 1 – Create the RSA Key Pair
Open the Terminal on your PC
Enter the following command in the terminal:
ssh-keygen -t rsa
Step 2 – Save the Keys and Passphrase
The above command will follow up with some confirmation messages
Enter file in which to save the key (/home/user/.ssh/id_rsa):
You can hit Enter, which will save the keys to the user home.
Enter passphrase (empty for no passphrase):
In this step, you will be asked for a passphrase for protecting your private key. We recommend you to add a passphrase since the whole point of setting up SSH is security. You will need to enter the passphrase every time you use the key pair.
If you do not want a passphrase associated with your private key, then simply hit enter leaving the passphrase field empty.
This will complete the key generation process:
ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/home/user/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/user/.ssh/id_rsa.
Your public key has been saved in /home/user/.ssh/id_rsa.pub.
The key fingerprint is:
4a:dd:0a:c6:35:4e:3f:ed:27:38:8c:74:44:4d:93:67 user@a
The key's randomart image is:
+--[ RSA 2048]----+
| .oo. |
| . o.E |
| + . o |
| . = = . |
| = S = . |
| o + = + |
| . o + o . |
| . o |
| |
+-----------------+
In the above example:
The private key’s location: /home/user/.ssh/id_rsa
The public key’s location: /home/user/.ssh/id_rsa.pub
Step 3 – Copy the Public Key to your node
Now you can copy and add your public key id_rsa.pub file, to set up SSH on your node under MyAccount.
You can usually get this key by copying the results of:
cat ~/.ssh/id_rsa.pub
Paste the results generated from id_rsa.pub to the SSH section under MyAccount.
You may add multiple SSH keys & can provide a label to each SSH key for easy identification & management purpose.
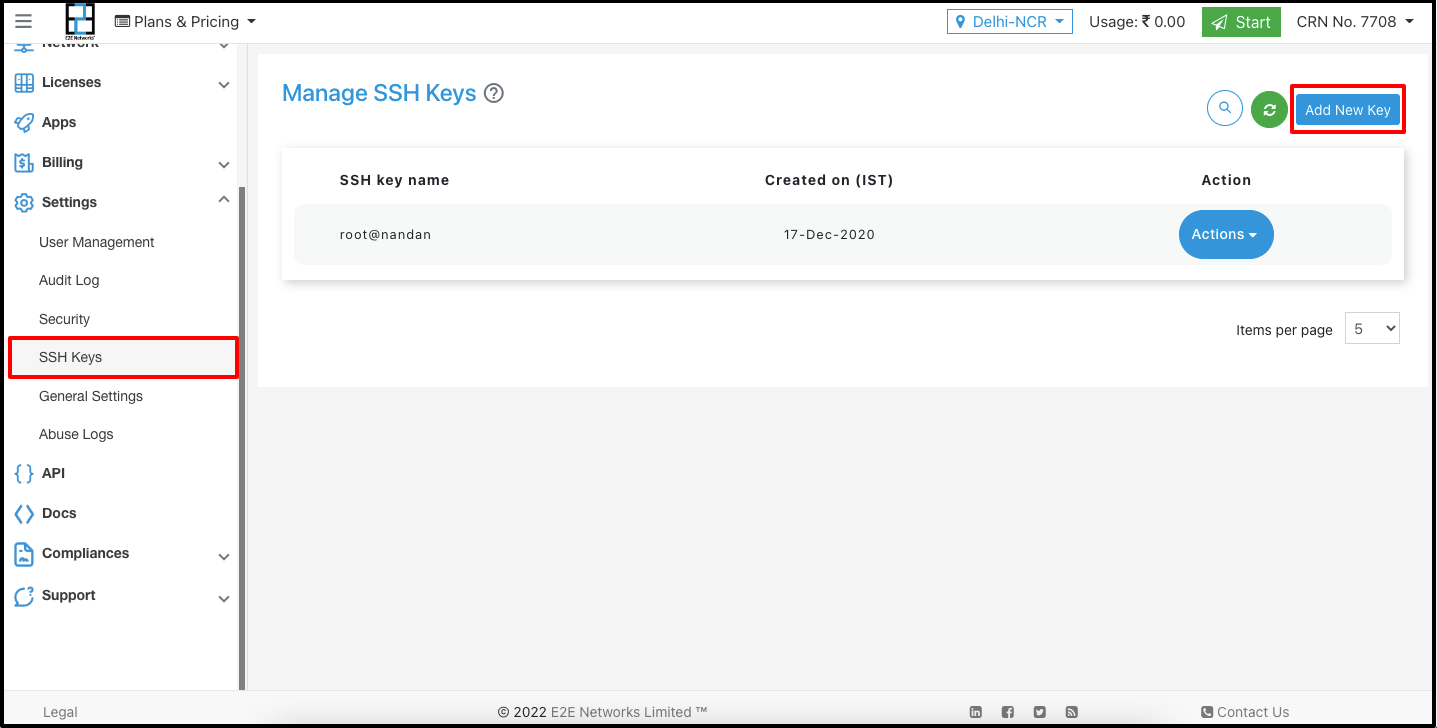
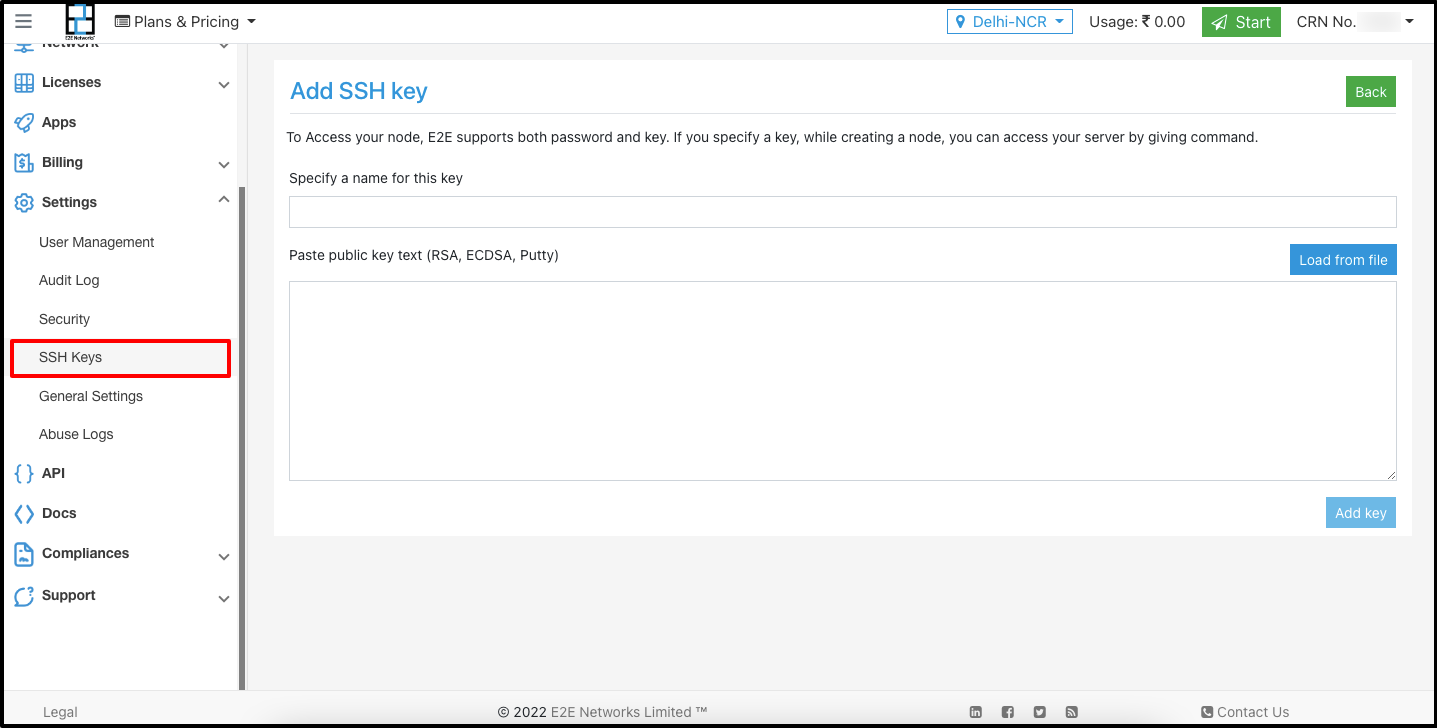
Copy the public key directly to a server (Alternate Approach)
The command ssh-copy-id can be used to install an authorized key on the server.
If you don’t have SSH access to the server then it will require a root password which is shared with you in the email.
Once the key has been authorized for SSH, it grants access to the server without a password.
Use a command like the following to copy SSH key:
Enter the following command to copy your public key to your Node:
ssh-copy-id user@xxx.xx.xx.xx
This will copy your public key to the authorized_keys file on your server.
Make sure to replace xxx.xx.xx.xx with your actual Ip address and replace user with your actual username in the above command.
Once you enter the ssh-copy-id command, you will see information similar to this:
The authenticity of host 'xx.xx.xx.xx (xx.xx.xx.xx)' can't be established.
RSA key fingerprint is b1:2d:33:67:ce:35:4d:5f:f3:a8:cd:c0:c4:48:86:12.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '12.34.56.78' (RSA) to the list of known hosts.
user@12.34.56.78's password:
Now try logging into the machine, with "ssh 'user@12.34.56.78'", and check in:
~/.ssh/authorized_keys
to make sure we haven't added extra keys that you weren't expecting.
Only the public key is copied to the server. The private key should never be copied to a machine.
Modifying permissions
For an additional layer of security, modify the file permissions.
Directory .ssh should have 700 permissions and authorized_keys file should have 400 or 600 permissions. To change the permissions, use the following commands:
# cd
# mkdir .ssh && touch .ssh/authorized_keys
# chmod 700 .ssh/ && chmod 600 .ssh/authorized_keys
# cat id_rsa.pub >> .ssh/authorized_keys && rm id_rsa.pub
Now log into the remote server using ssh or scp/sftp:
# ssh username@< server-ip >

