How to Configure Application Load Balancer
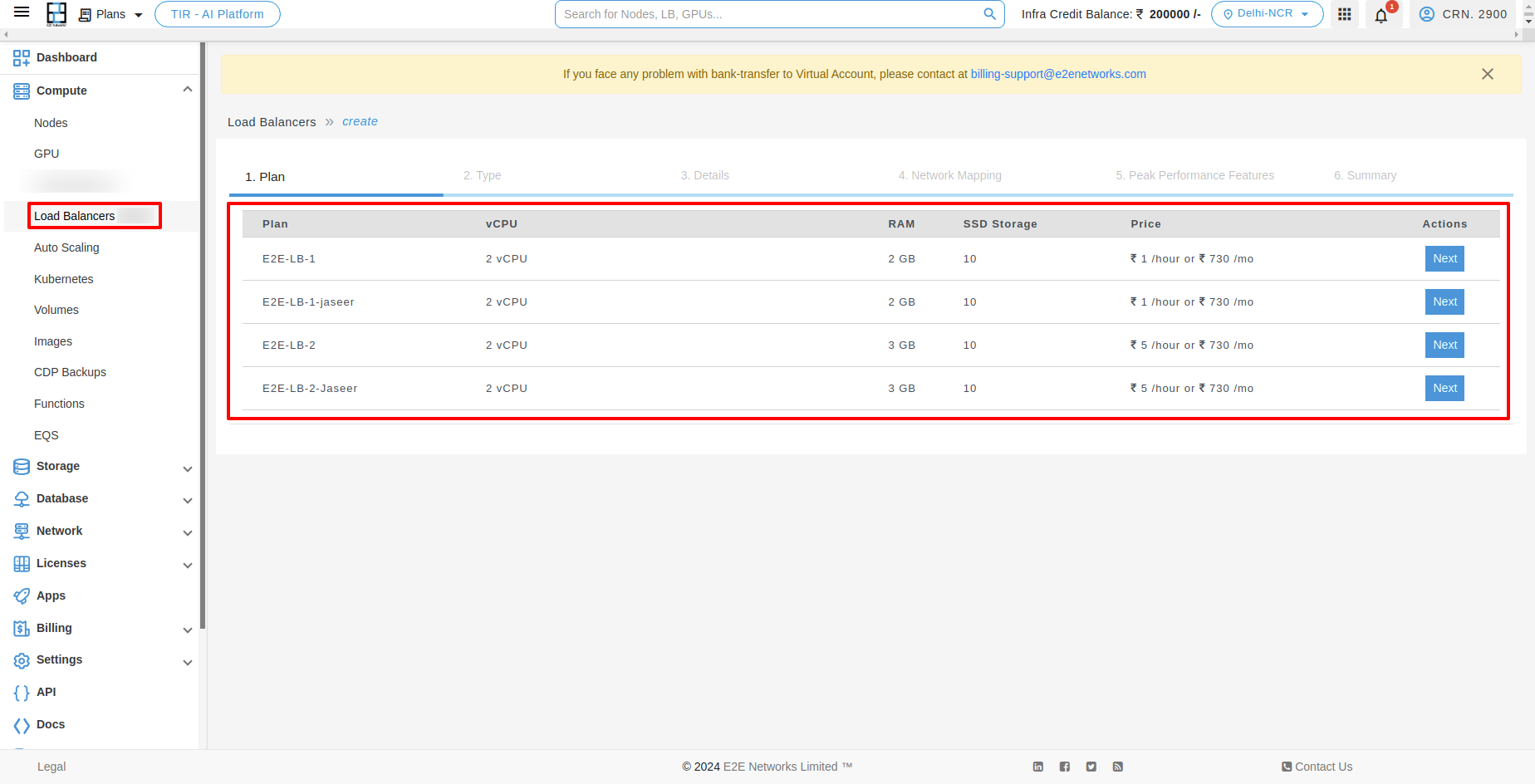
Select your Load Balancer Plan
All the load balancer plans are listed based on different memory, vCPU and storage configuration and price.
Please select a plan you wish to use to create the new load balancer.
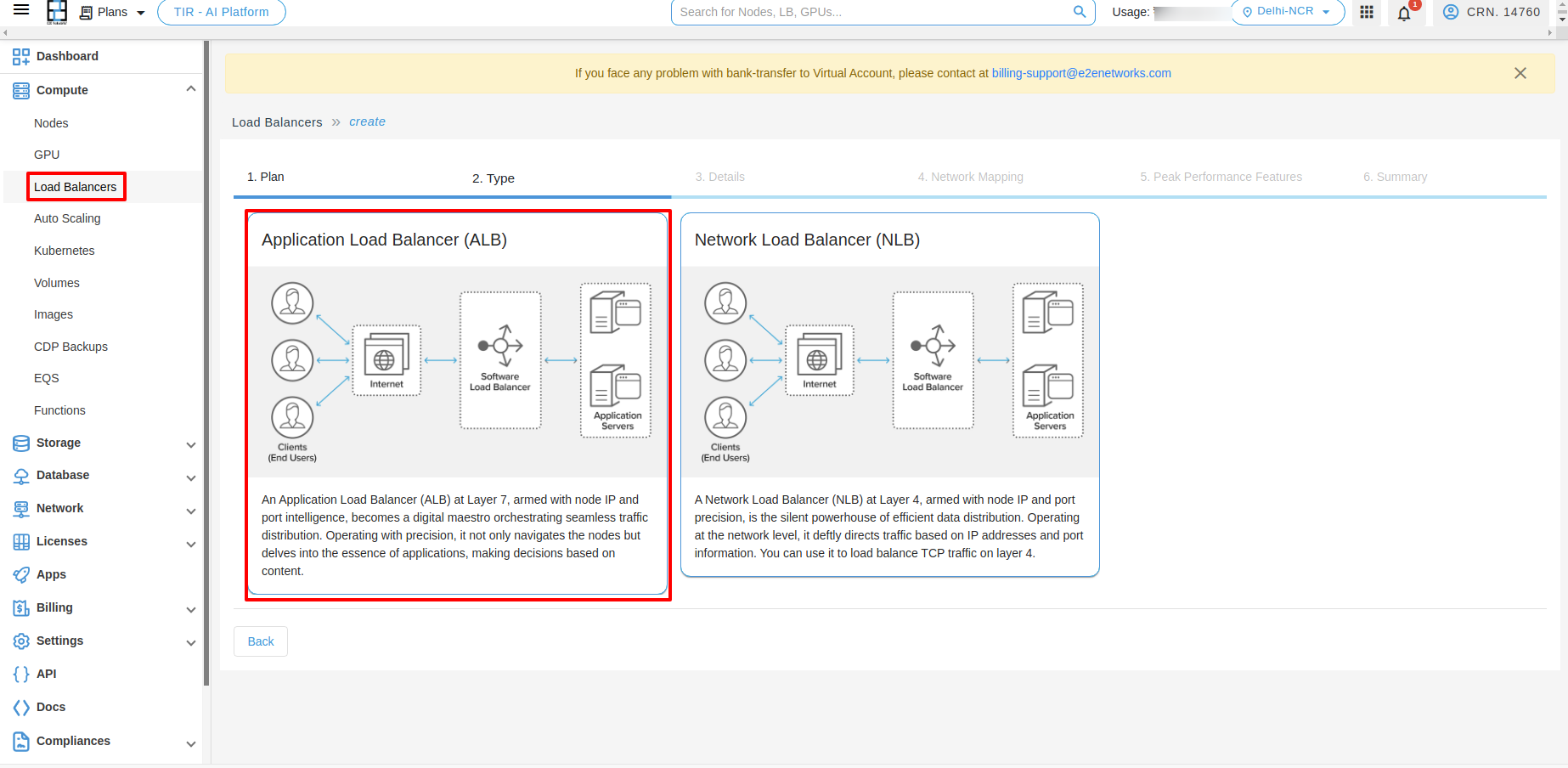
Type
After selecting the plan, you need to choose the Application Load balancer type.
Details
Name - Default name is provided based on the Plan you selected, but you can modify and give a string of characters that you can enter as the name of your Load Balancer Appliance.
Type - Select the type for your load balancer Internal or External according to your requirement.
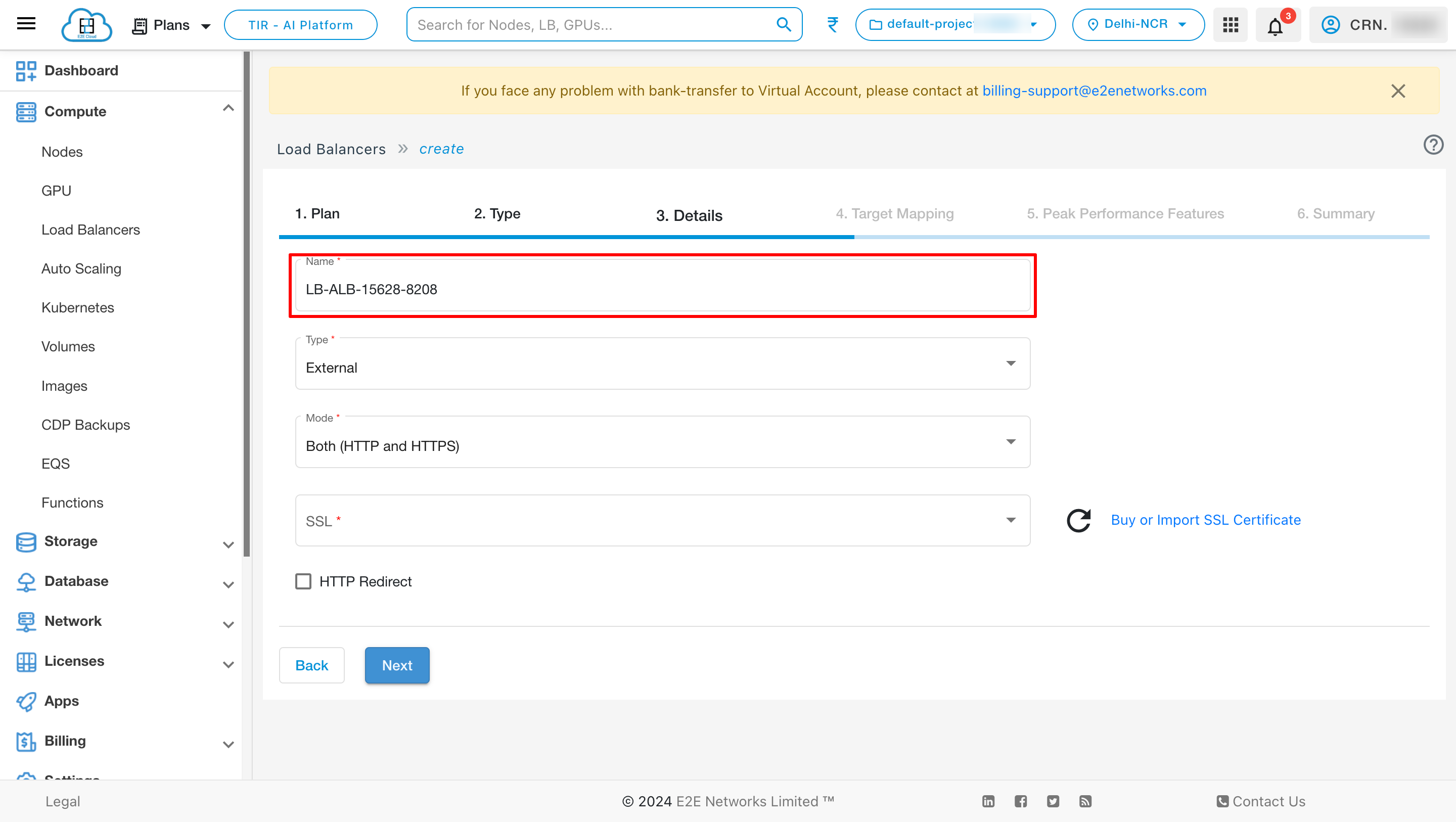
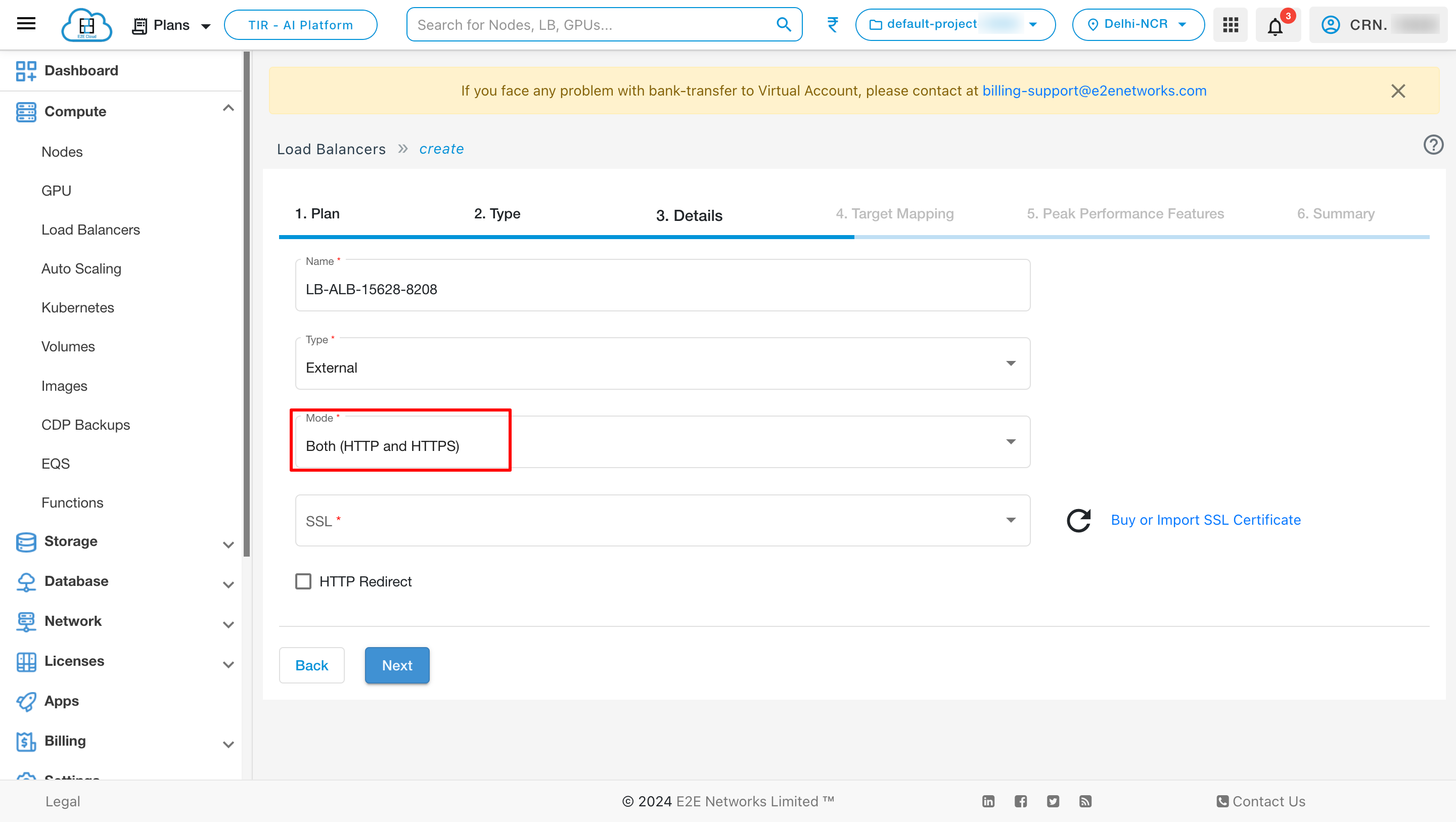
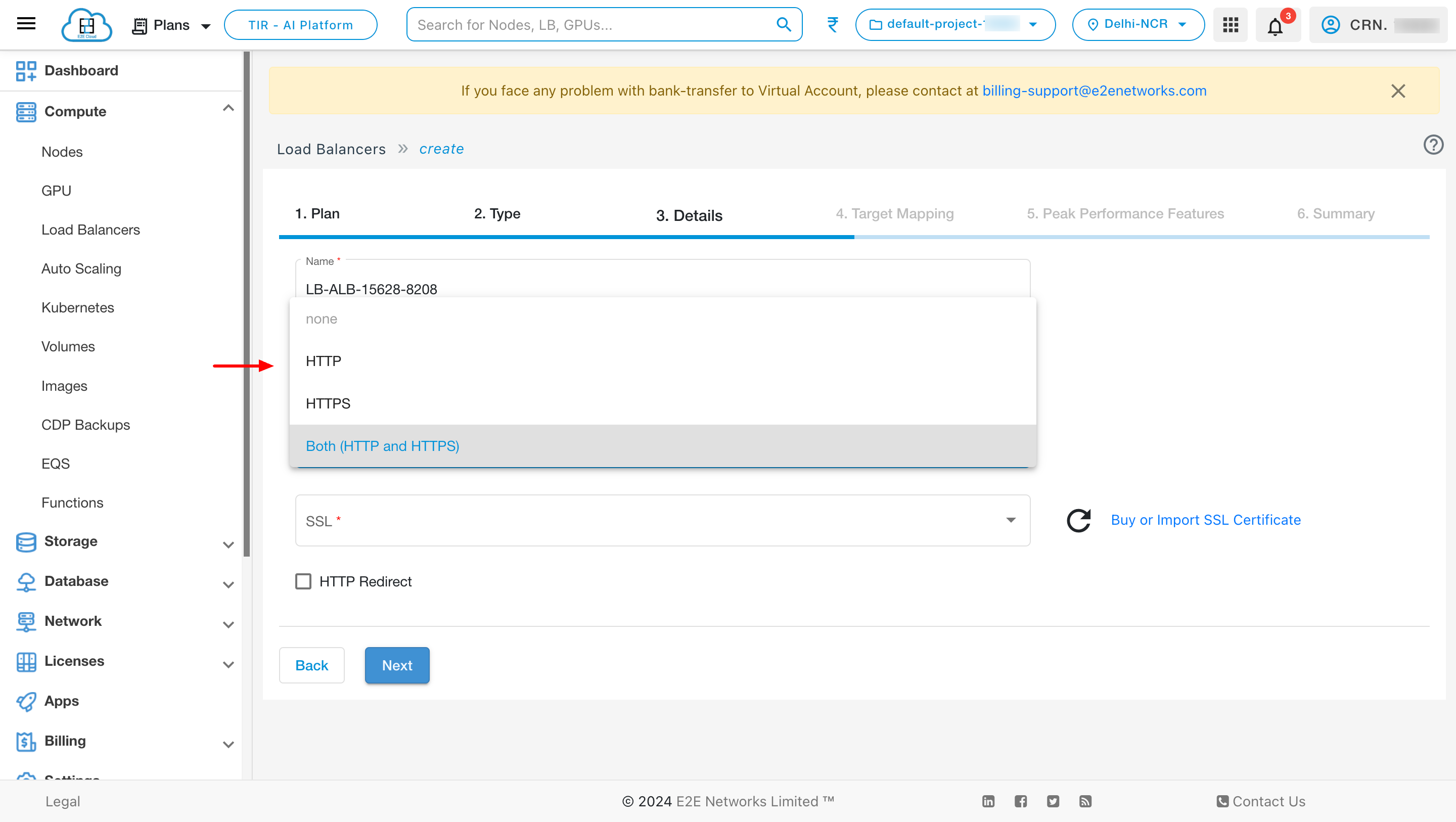
Mode
Choose Mode - Mode is a process that checks for connection requests using a specified protocol and a port for front-end (client to load balancer) connections. E2E Networks Load Balancer supports the following protocols.
Support both HTTP and HTTPS protocol independently
HTTPS (secure HTTP) using SSL/TCL: Supports the X-Forwarded headers and Requires an SSL certificate deployed on the load balancer.
HTTP: Supports the X-Forwarded headers.
Note
For the back-end (load balancer to nodes) connections of a load balancer HTTP protocol by default is used.
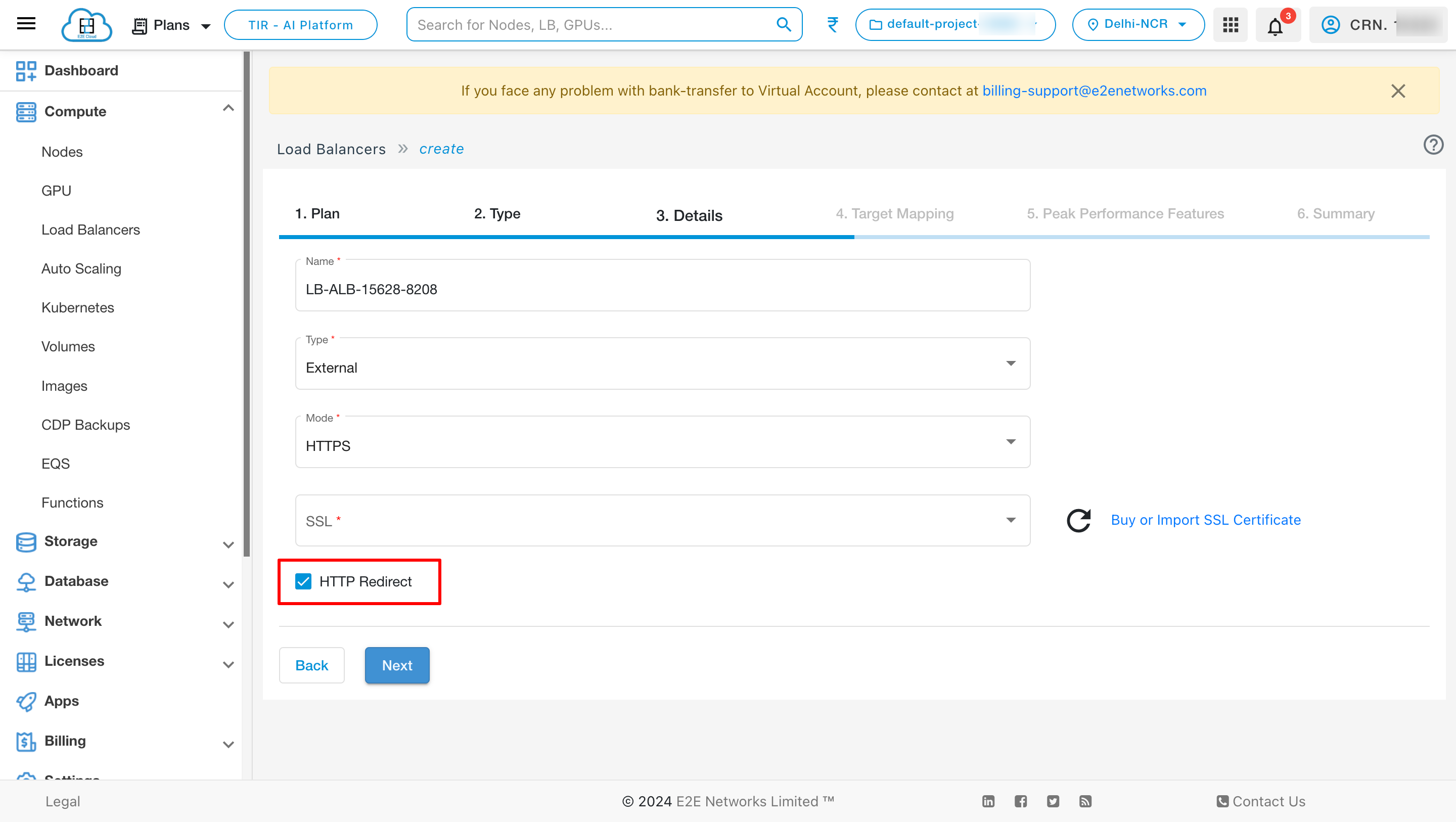
HTTP Redirect
Select Redirect HTTP to HTTPS checkbox, If you use “HTTPS (SSL or TLS)” for your front-end protocol of load balancer. For your web user safety, accessibility or PCI compliance, it becomes essential to enable redirect from HTTP to HTTPS to redirect all your traffic to LB from HTTP to HTTPS.
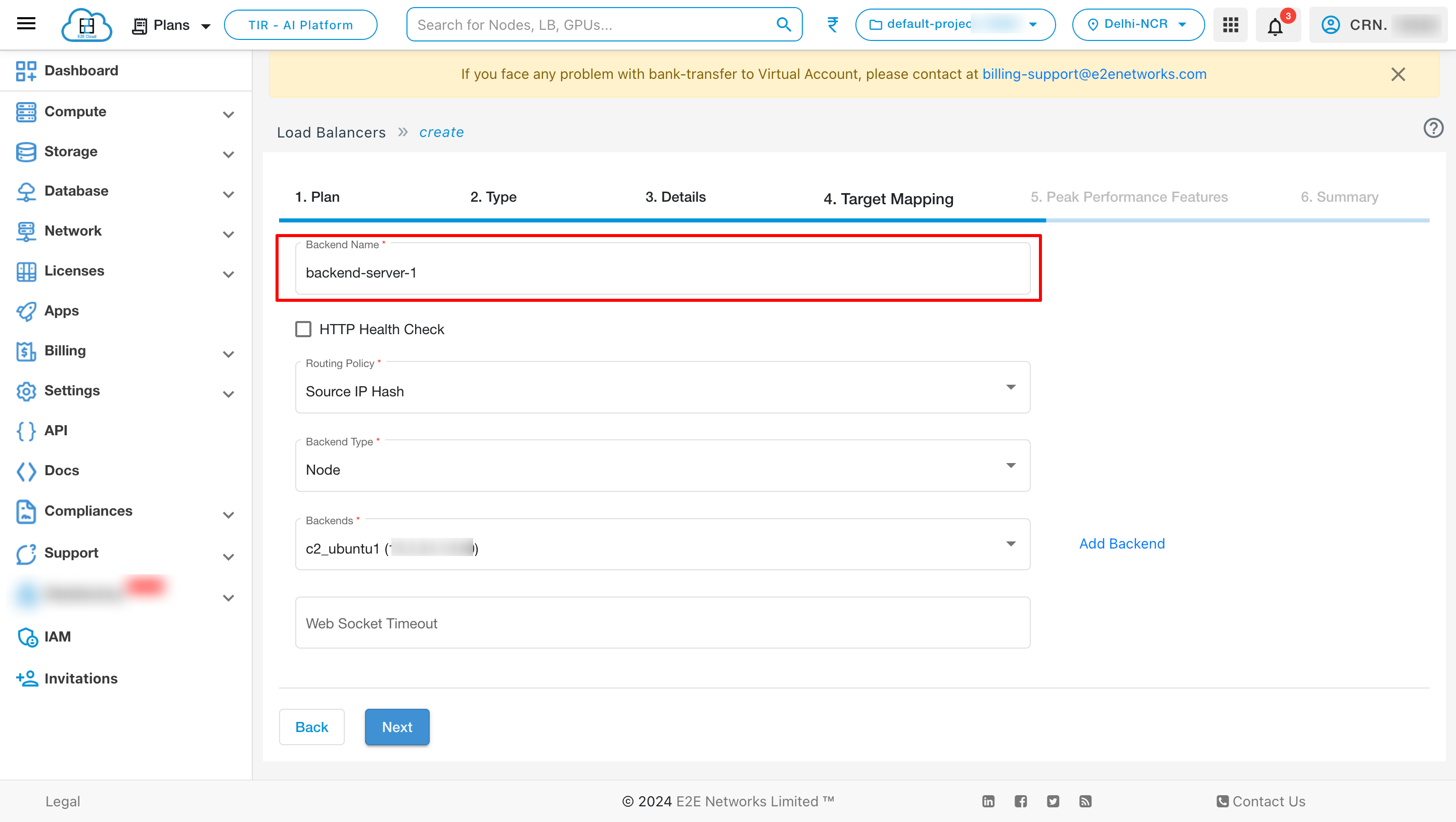
Target Mapping
Backend Name
Health Check
Your load balancer checks the health of the web application configuration that you specify. The health check configuration contains information such as the domain, and health URL. If the backend node responds with 2xx or 3xx HTTP status code for the defined URL path, it will mark as UP; else DOWN. By default, Load Balancer checks the connectivity to the backend-nodes/Target port defined during creation to mark a backend node up or down for it. If any node is down/unresponsive, traffic will not send to that particular node. The removal of unresponsive nodes and their re-addition on successful health checks are automatically taken care of by the Load Balancer appliance.
Select Add HTTP Health Checks checkbox to define an HTTP based monitoring for the health of your backend nodes.
You need to define a URL path to which HTTP HEAD requests will send to fetch the response code. If the backend node responds with 2xx or 3xx HTTP status code for the defined URL path, it will mark as UP; else DOWN.
Note
The default URL path is / which means the index page of your site/application hosted on the backend nodes, and it can be changed to any other URI path as well.
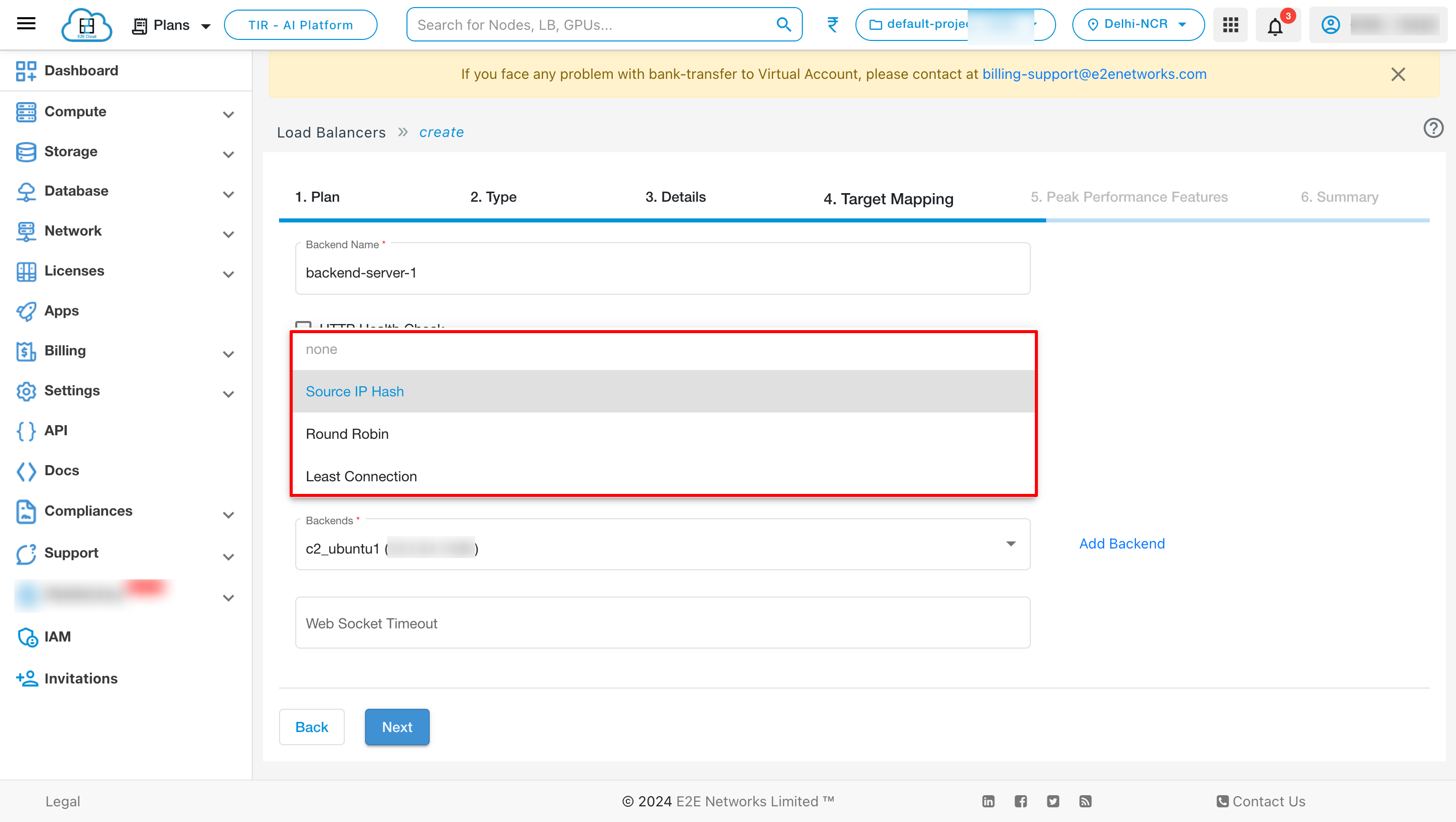
Routing Policy
Choose Balancing Policy - Different load balancing policy algorithms provide different benefits; the choice of load balancing method depends on your needs. Please select the balancing method either “Source IP Hash” or “Round Robin” based on your use case.
Round Robin Method : This method selects the backend servers in turns distributing the connection requests evenly among them.
Source IP Hash : This method selects which backend server to use based on a hash of the source IP, i.e. a user’s IP address, ensuring that a user will connect to the same backend server.
Least Cnnection : The term “least connection” in the context of load balancers refers to a specific load balancing algorithm used to distribute incoming traffic among available servers. Here’s how it works:
How Least Cnnection works :
1. The load balancer keeps track of the number of active connections to each server in its pool.
2. When a new connection request arrives, the load balancer selects the server with the least number of active connections at that moment.
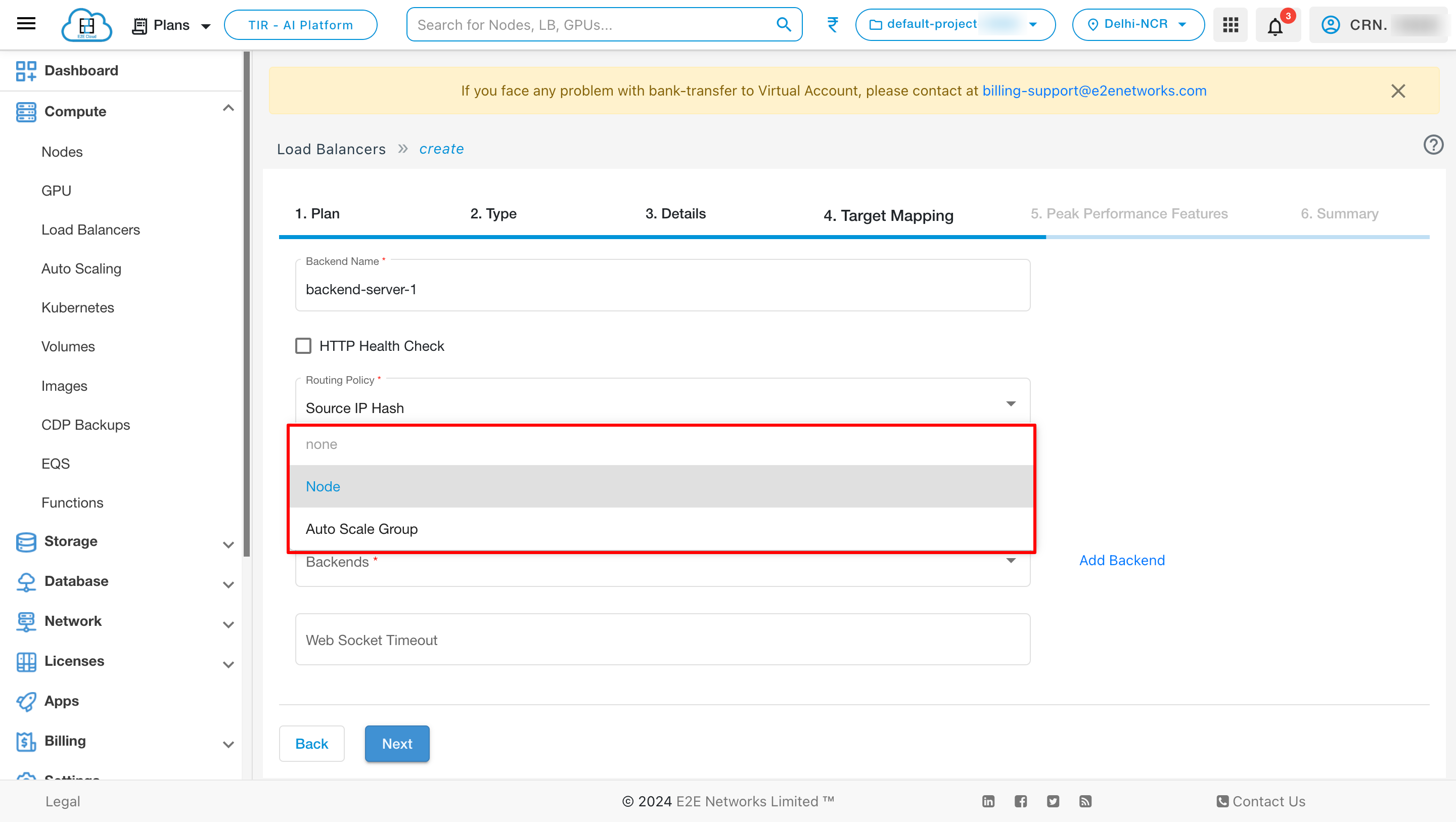
Backend Type
In the List Type, you can select either Node or Auto Scale Group (for Auto-scaling group nodes only) to configure backend connection of your load balancer as per your requirement.
1. Node
Registering an E2E node adds it to your load balancer. The load balancer continuously monitors the health of registered nodes and routes requests to the nodes that are healthy. You can register or deregister nodes with the load balancer to handle the demand.
Select the Node in the list type field. The node details section will be displayed.
In the Node Details section, you need to specify the details of the virtual nodes you wish to register behind the Load Balancer. For this, please enter the node’s name, node’s IP(preferably private IP if the backend node created on E2E cloud), and specify the port to which you want to send/receive traffic via Load Balancer.
Add Backend
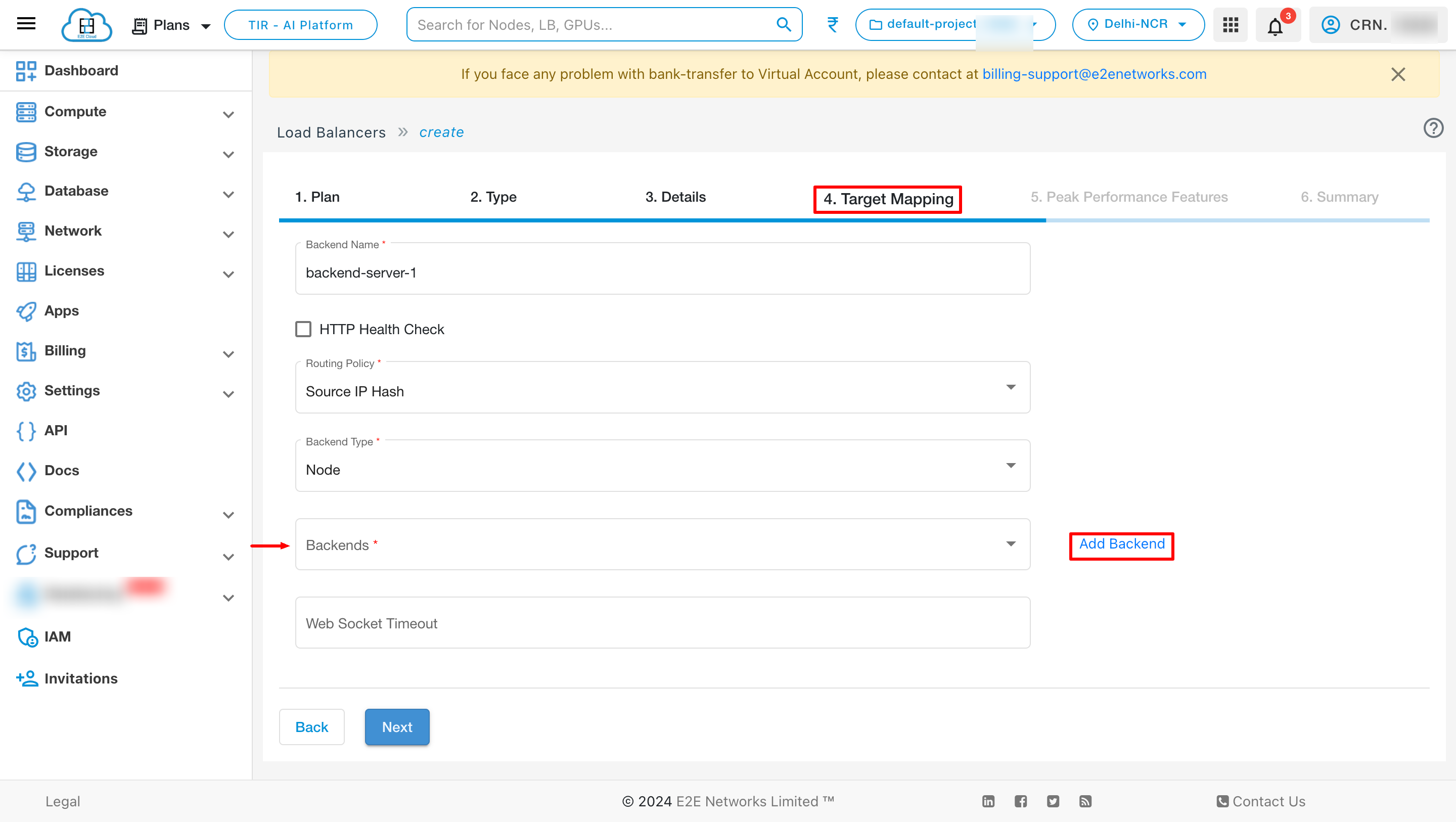
You can add backend by clicking Add Backend button
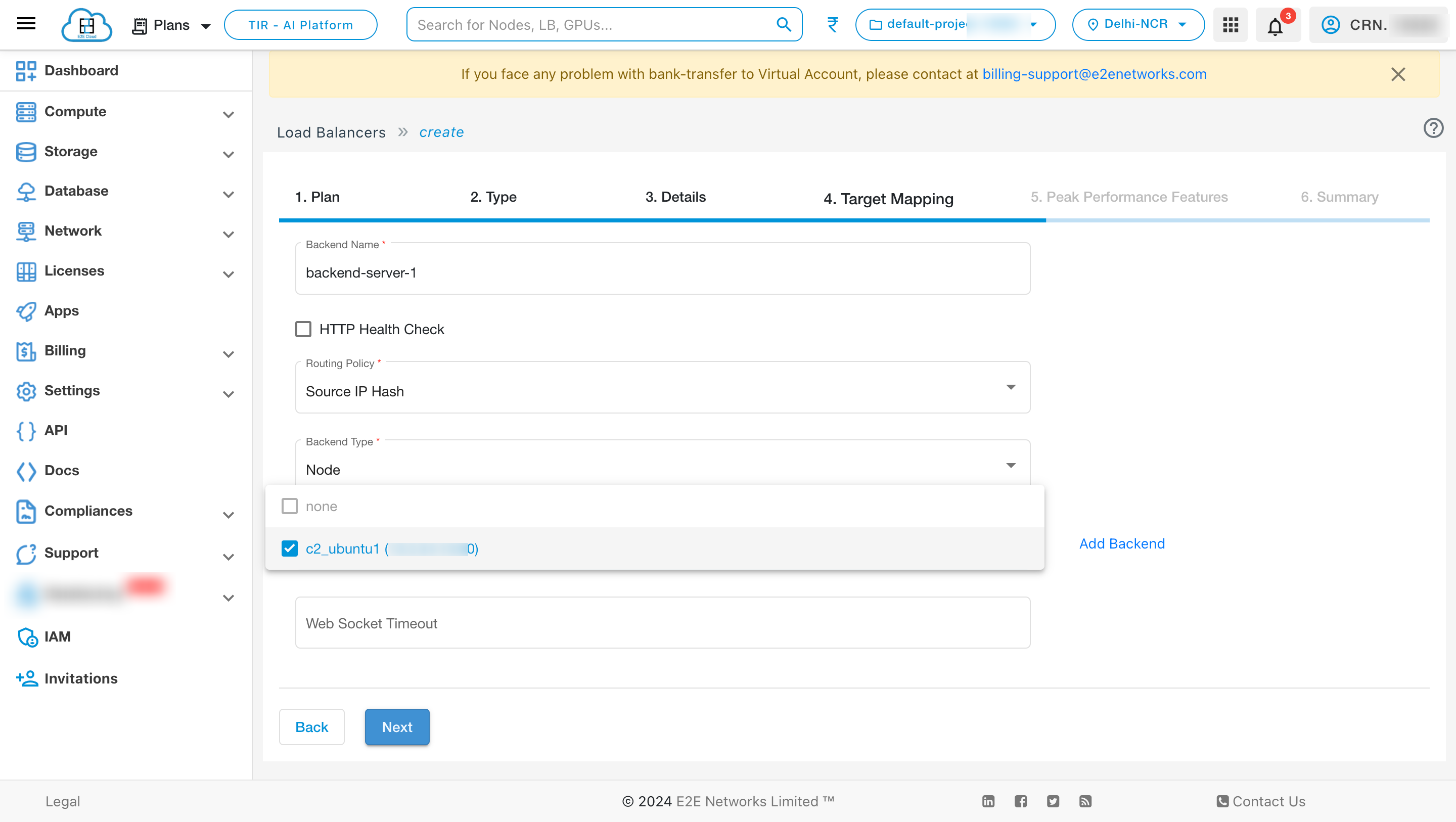
After adding backends, you can see the list of backend by clicking the dropdown.
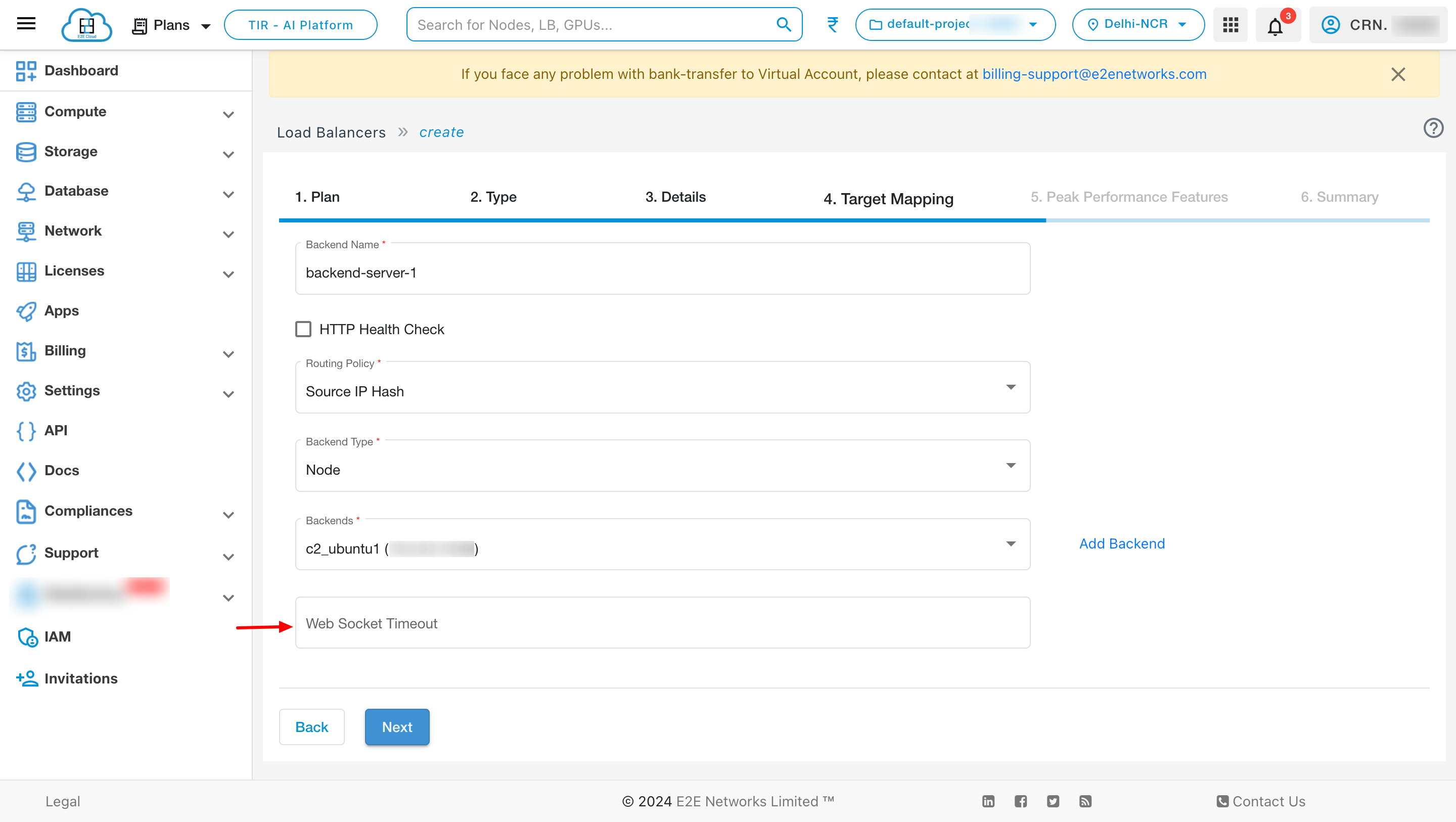
You can also give websocket timeout for an ALB.
2. Auto Scale Group
Registering your Auto Scaling group with a load balancer helps you set up a load-balanced application because EAS enables you to dynamically scale compute nodes based on varying workloads and defined policy. Using this feature, you can meet the seasonal or varying demands of infrastructure while optimising the cost and distributing incoming traffic across your healthy E2E nodes—the scalability and availability of your application increases.
Select the Dynamic Scale group in the list type field. The node details section will be displayed.
In the Scale Group Details section, you need to select an application scaling group from the dropdown list you wish to register behind the Load Balancer.
After selecting the scale group, define the port to which you want to send/receive traffic via Load Balancer in Target Port field.
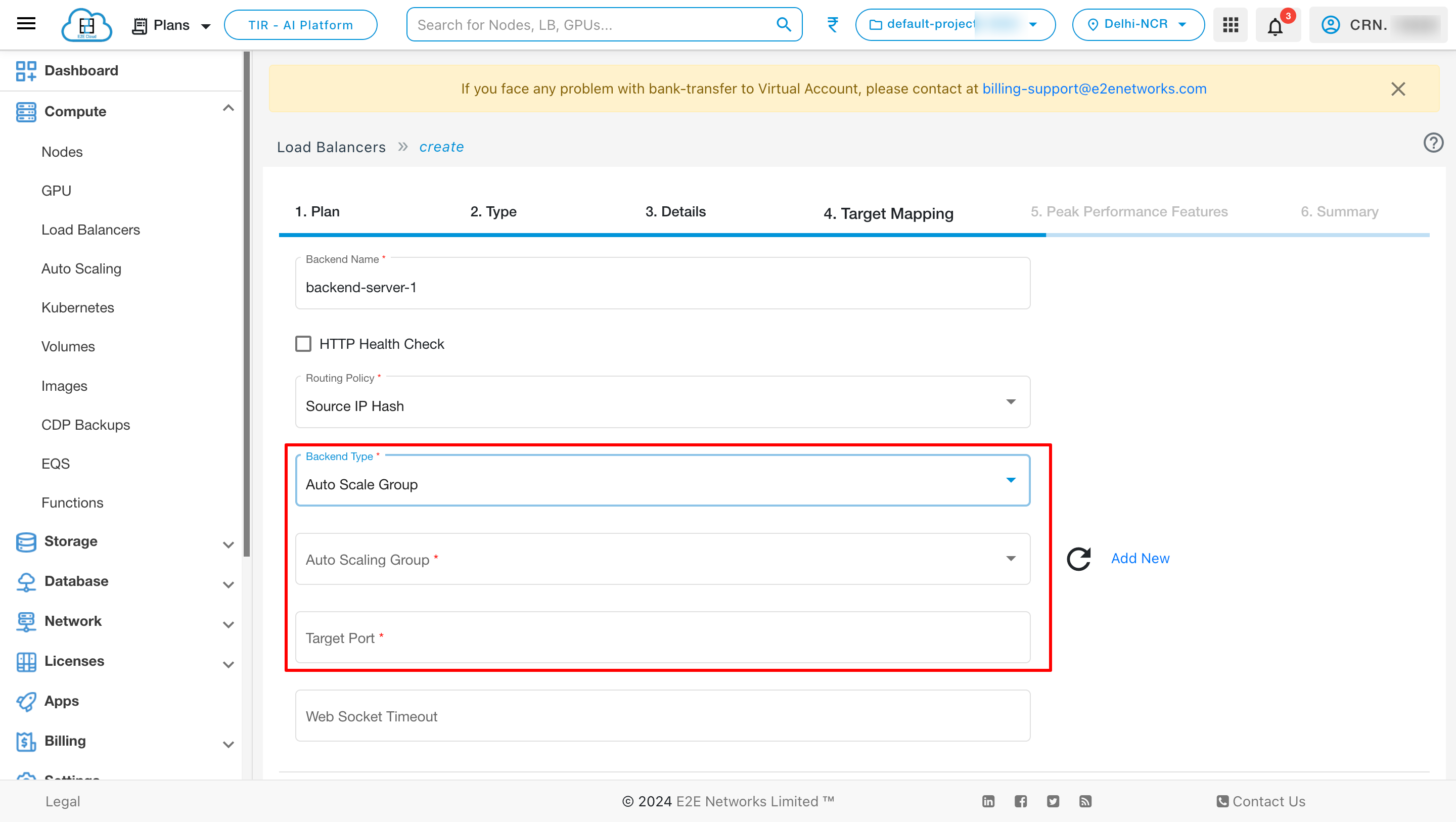
To add auto scaling group click on Add New
Peak Performance Features
Create New VPC - Enable this option to use a VPC IP as default VPC IP for your load balancer to connect your LoadBlancer internally.
After creation of VPC you can see the created VPC on dropdown list.
Add New Reserve IP - Enable this option to use a reserved IP as default Public IP for your load balancer. For example, you can dynamically update the backend resources of your applications and websites by re-assigning the reserved IP address without a downtime.
After creation of IP you can see the created IP on dropdown list.

BitNinja
BitNinja is an easy-to-use server security tool mixing the most powerful defense mechanisms. Every BitNinja protected load balancer learns from every attack and the system applies this information automatically on all BitNinja enabled servers/ load balancer. This way the shield is getting more and more powerful with every single attack. Learn more
Enable Bitninja - Enable this option to use a bitninja security tool for your load balancer. BitNinja has different modules for different aspects of cyberattacks. It is super easy-to-install, requires virtually no maintenance and able to protect any server by providing immediate protection against a wide range of cyberattacks.
Timeouts
You can also give different timeout values like connection timeout, client timeout, server timeout and HTTP keep alive timeout according to your requirement.
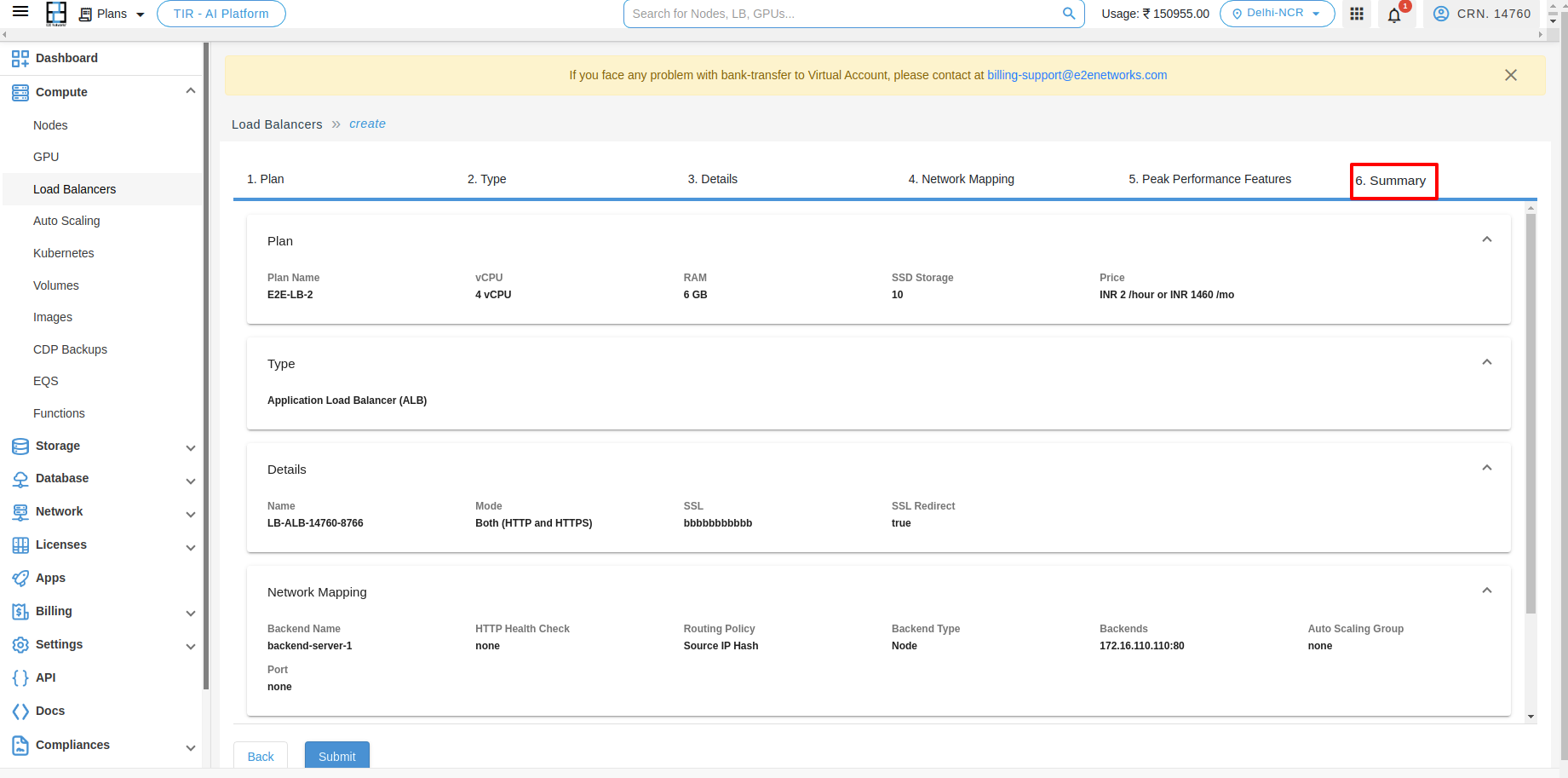
Summary
In that summary section, you can verify your Plan, Type, Details, Network Mapping, Peak Performance Features.
Deploy Load Balancer
After filling all the details successfully, click on the Submit button. It will take a few minutes to set up the scale group and you will take to the ‘Load Balancers’ page.
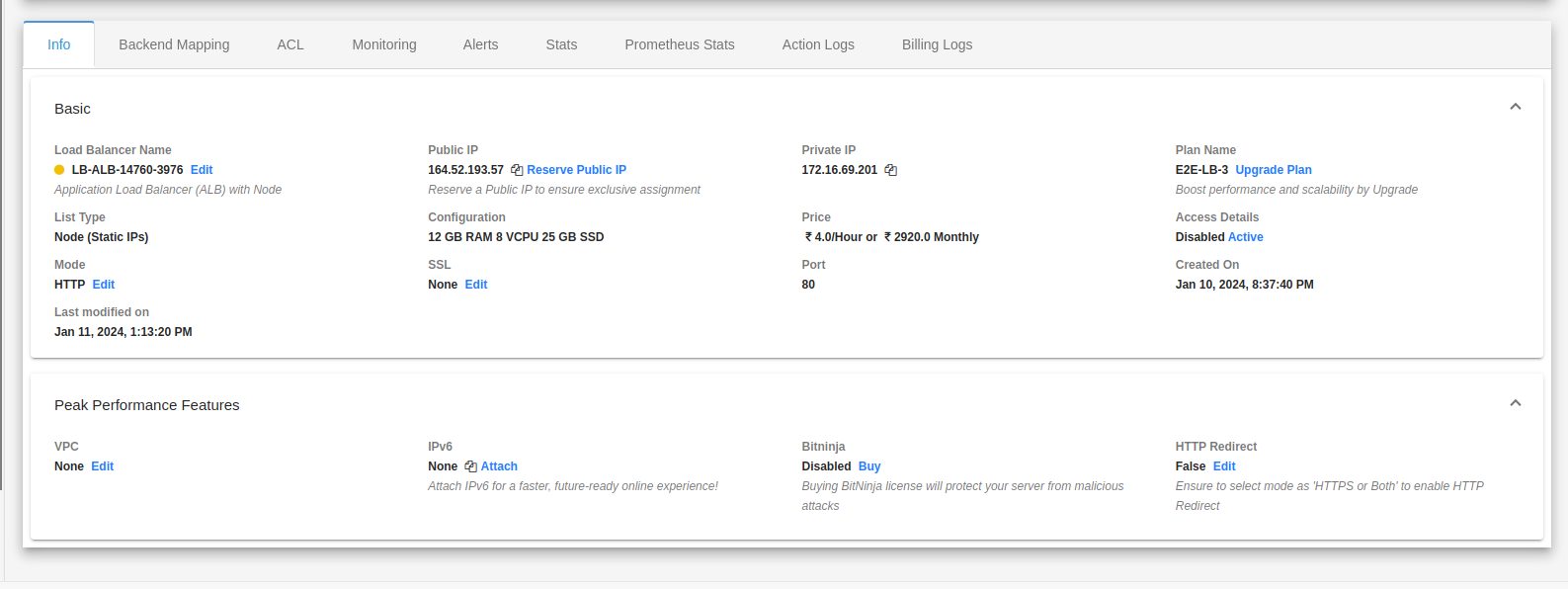
Application Load Balancer Info
You can check all the basic, security, backend configurations and networks details of your load balancer on the Load balancer info tab.
Backend Mapping
Once you have created your load balancer, you can access and manage load balancer from My Account Portal. Click on installed LoadBlancer instance and below you can see the various options to manage your installed LoadBlancer instance.
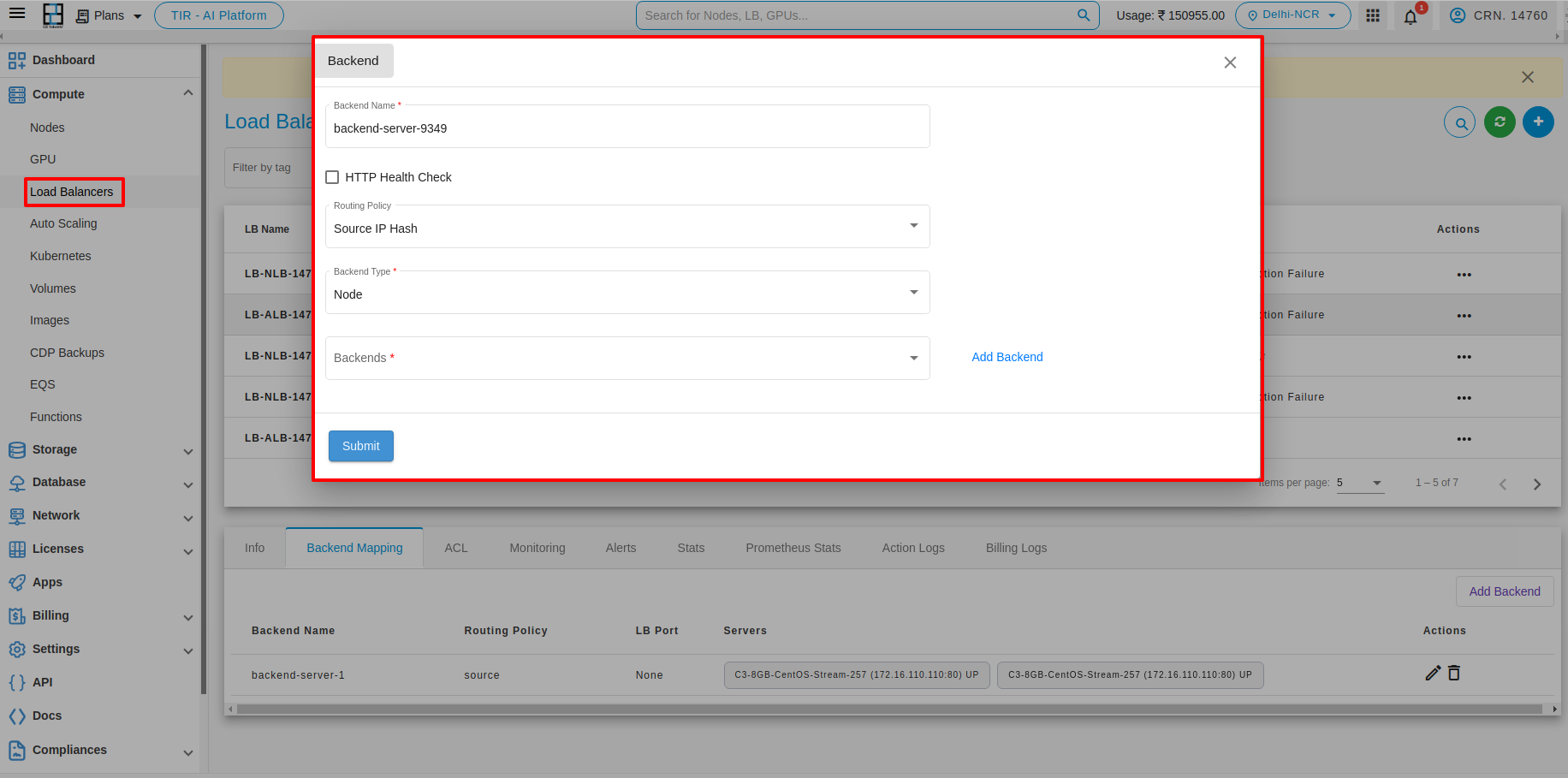
To add backend, click on Add Backend button.
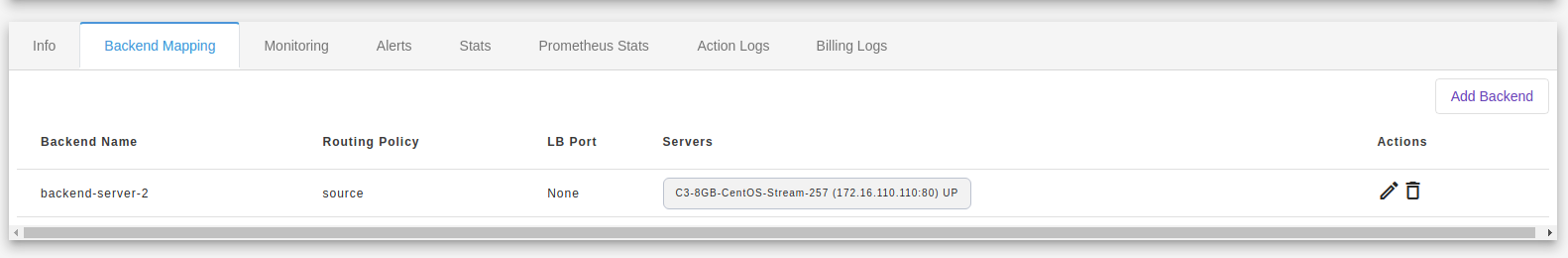
After adding the backend you can see the list below.
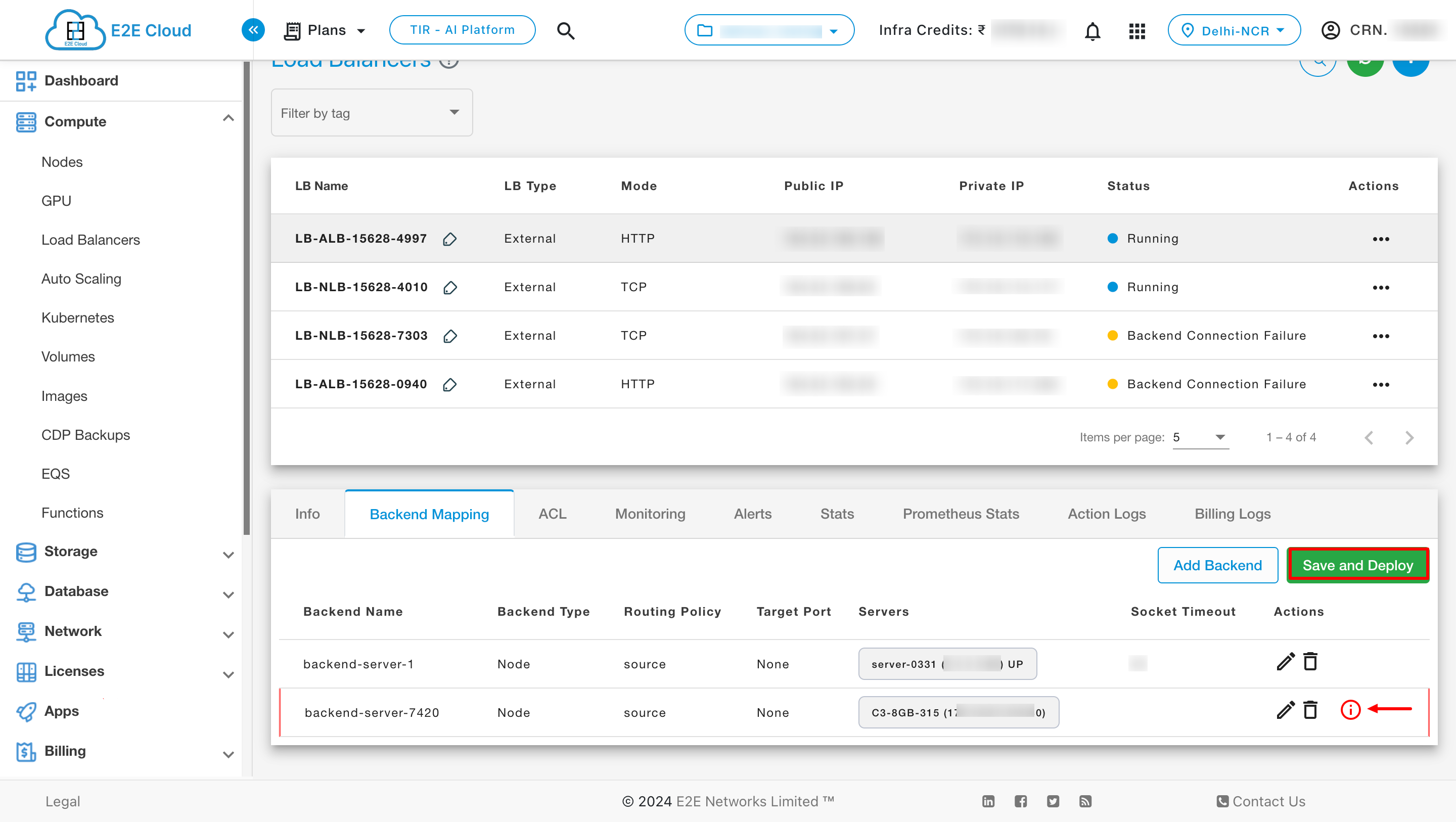
Users can add or edit multiple backends simultaneously. Upon making desired edits, a “Save and Deploy” button will appear. Additionally, an info icon will be displayed next to the backend where changes have been made. Click on the “Save and Deploy” button to save your changes.
You will be redirected to the Edit Load balancer page. You can add/change backend and frontend configuration of your load balancer.
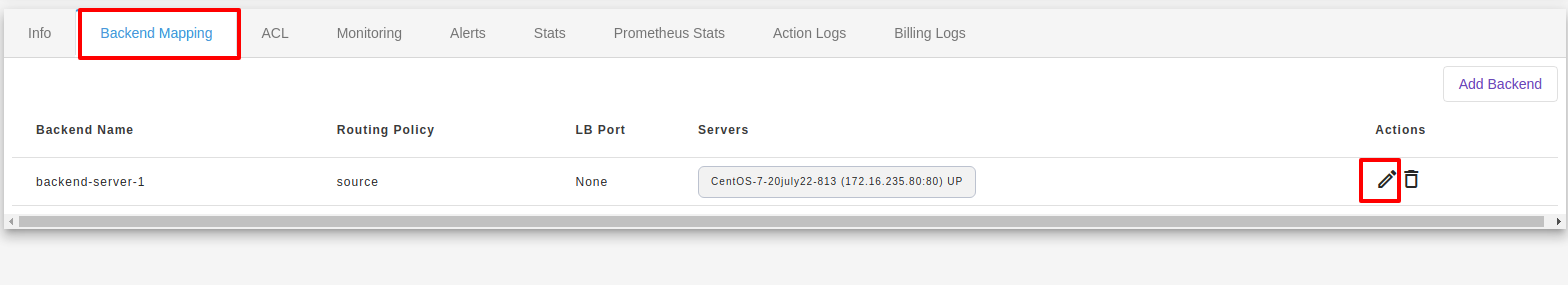
You will be redirected to the Delete Load balancer page. You can delete backend and frontend configuration of your load balancer.
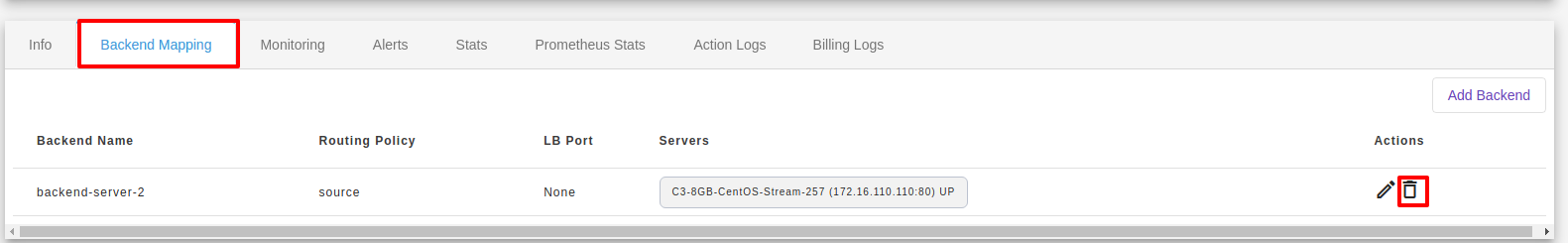
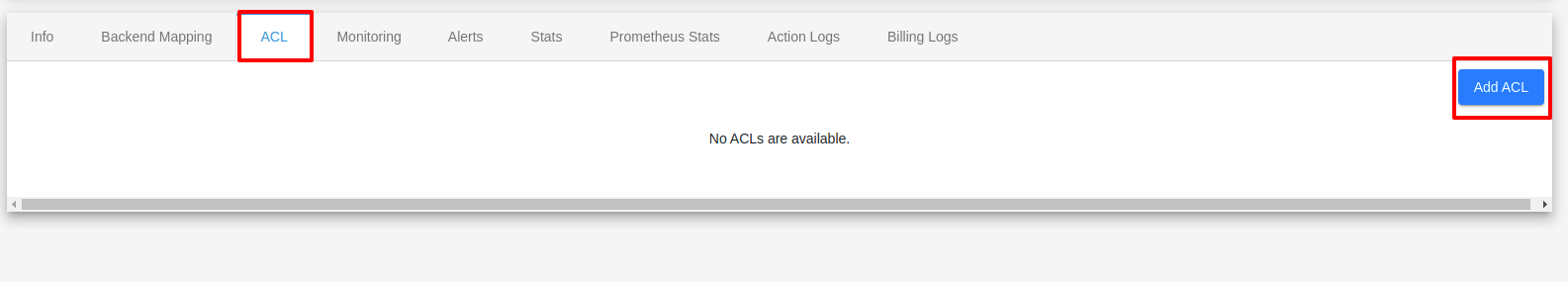
ACL
You can add ACL by clicking ADD ACL button under ACl tab.
Users have the option to add multiple ACL rules simultaneously. After making desired edits, a “Save and Deploy” button will appear. Additionally, an info icon will be displayed next to the newly added rules. Click on the “Save and Deploy” button to save your changes.
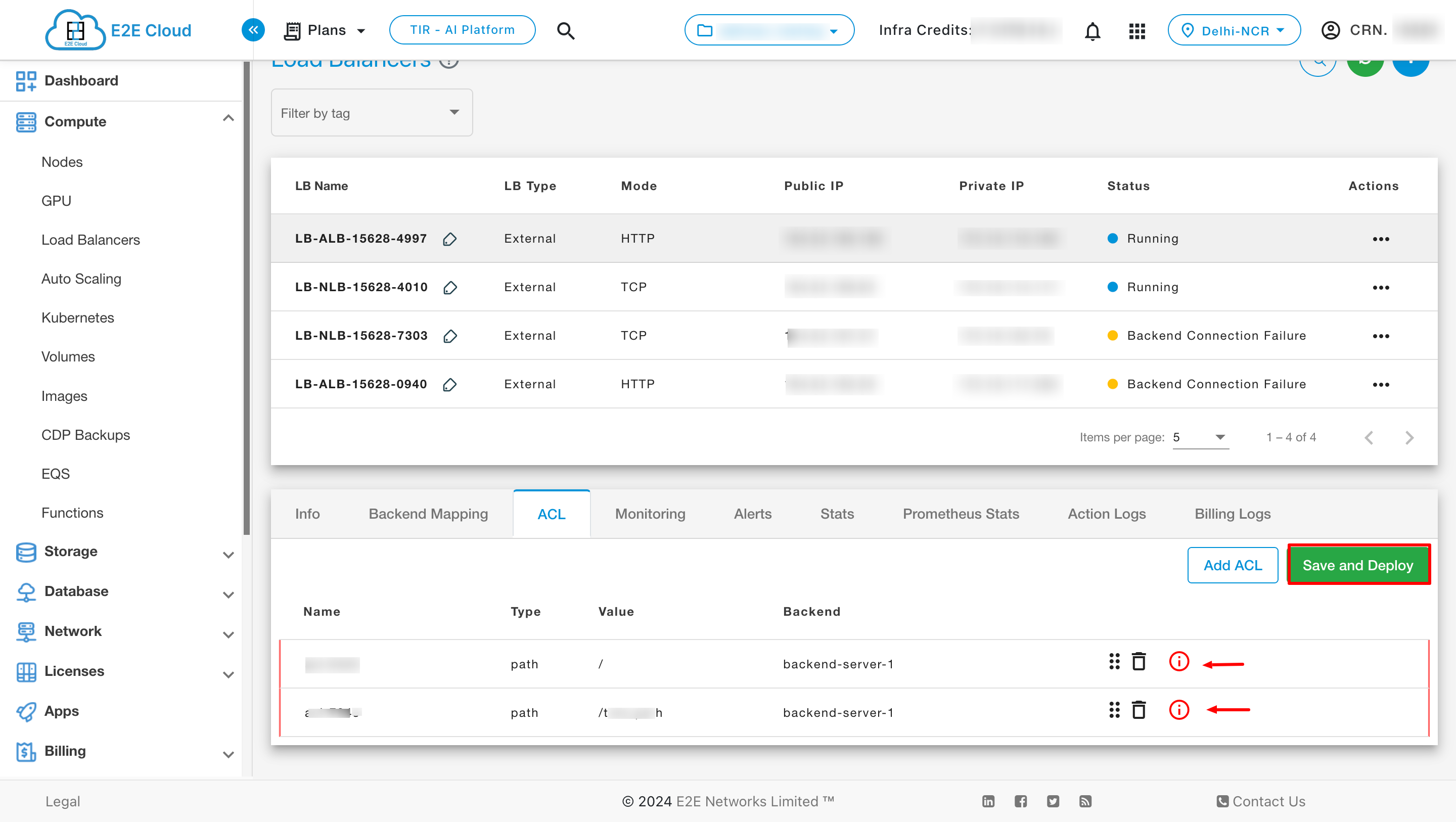
Access rules can be added based on five conditions.
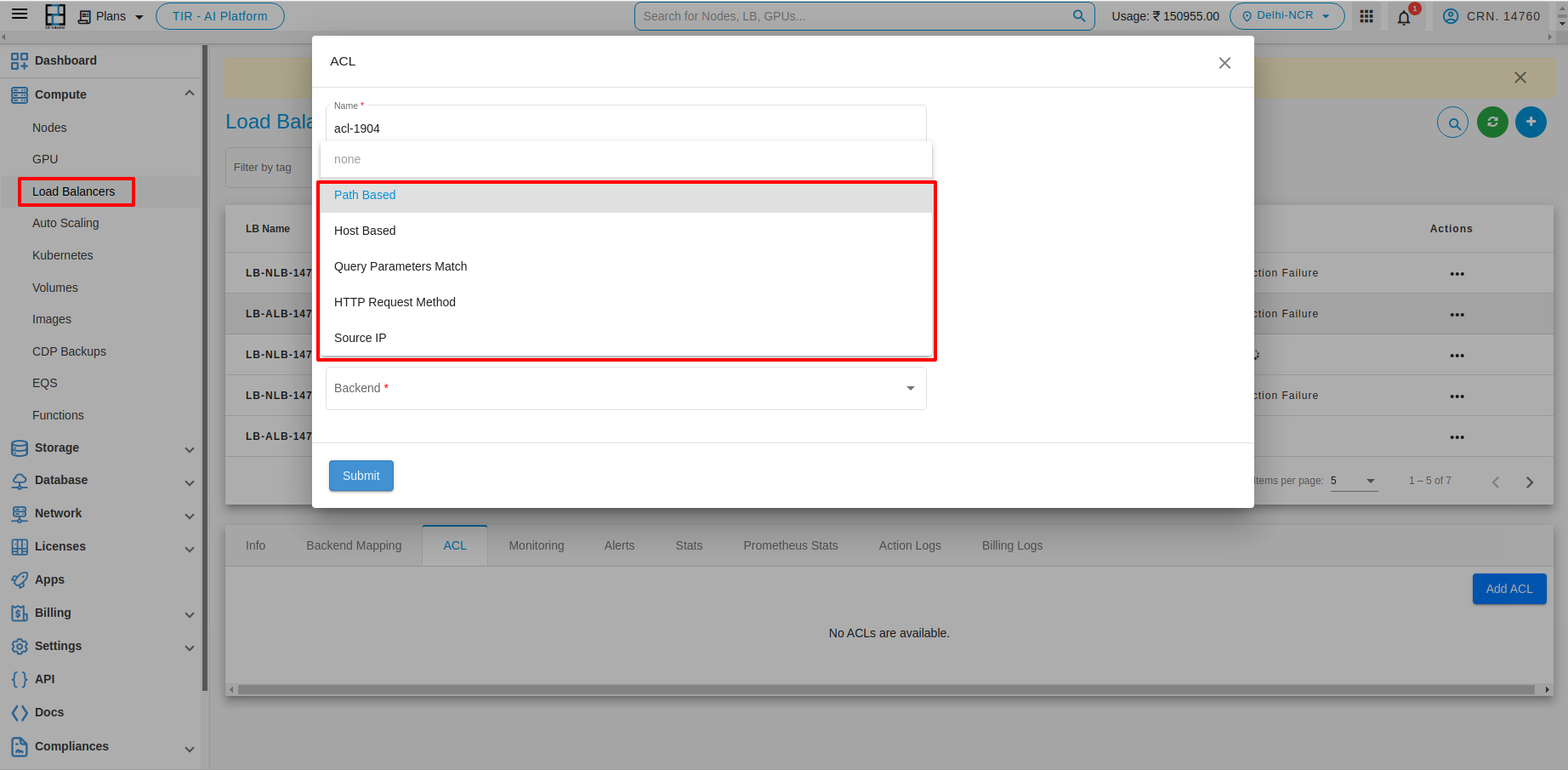
Path Based Condition
Host Based Condition
Query parameters Match
HTTP Request Method
Source IP
1. Path Based : - You can use path conditions to define rules that route requests based on the URL in the request. The path pattern is applied only to the path of the URL, not to its query parameters. For example, In the below image the path is added e2enetworks.com/test
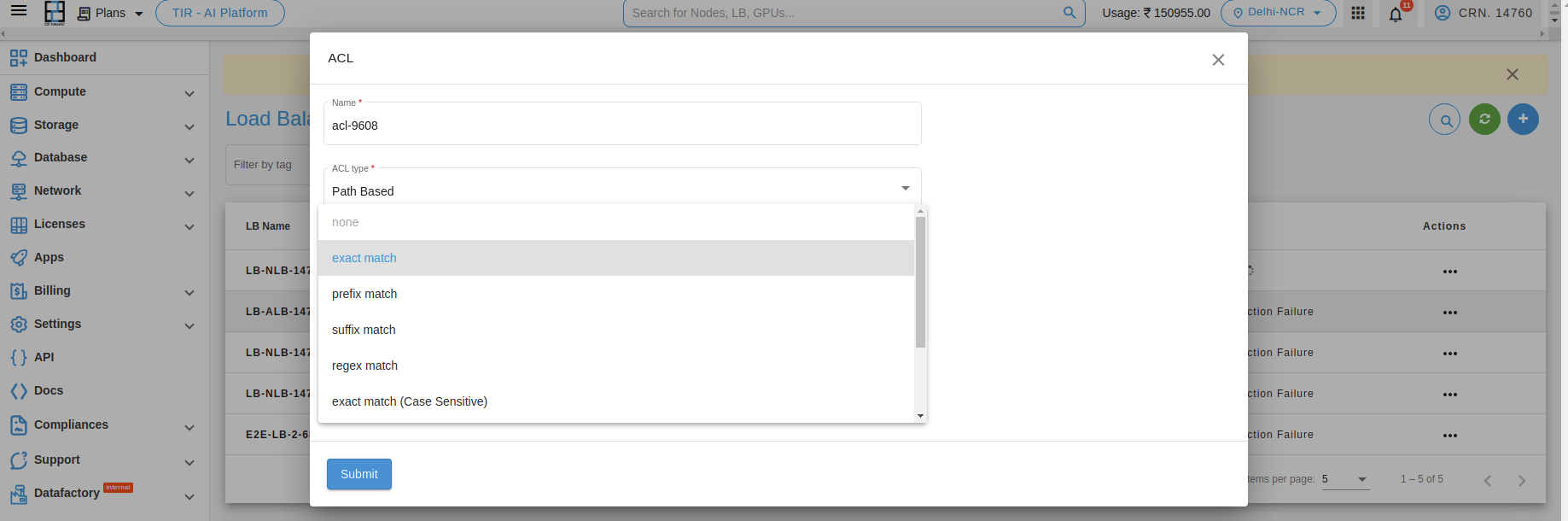
- 1. Exact Match : An exact match will only match the exact word “pathbase”.
Example: “pathbase”
- 2. Prefix match: A prefix match will match any word that begins with “pathbase”.
Example: “pathbasefolder”, “pathbaseconfig”, “pathbasedirectory”
- 3. Suffix match: A suffix match will match any word that ends with “pathbase”.
Example: “datapathbase”, “sourcepathbase”, “projectpathbase”
- 4. Regex match: A regular expression can be used to match words that contain “pathbase”.
- Example: bw*pathbasew*b:
This regular expression will match any word that contains “pathbase” as a separate word. For example: “pathbasefile”, “mypathbaseproject”, “datapathbaseconfig”, “pathbase123”.
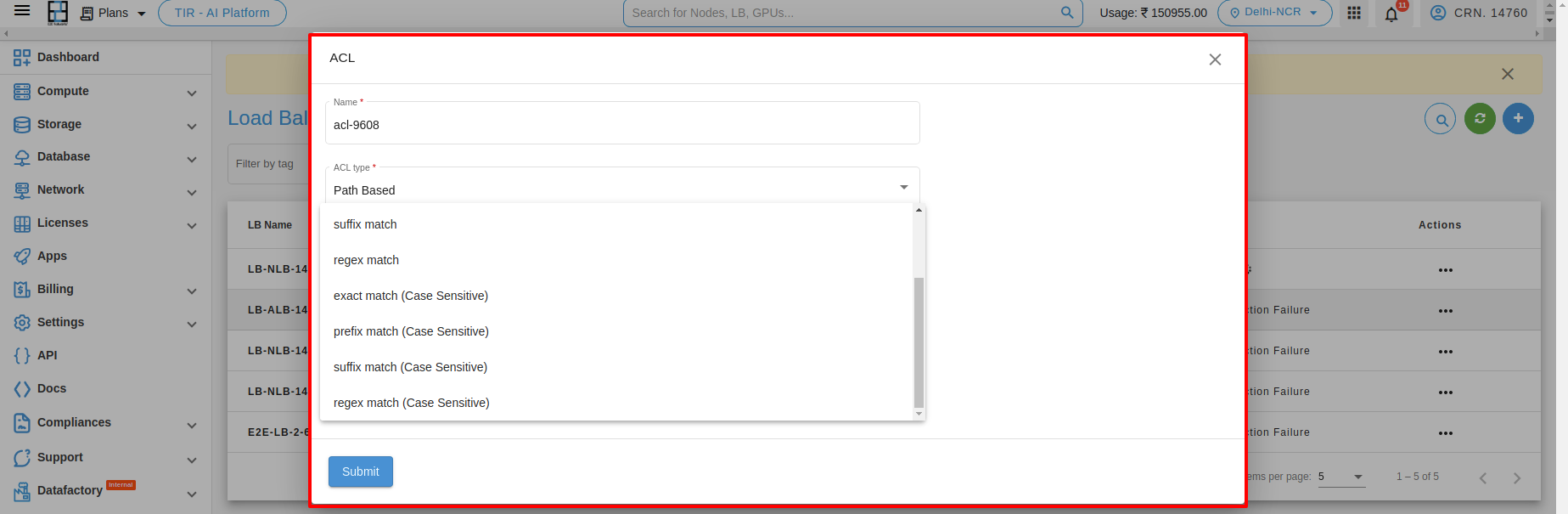
- 5. Exact match (Case sensitive) : An exact match will only match the exact word “pathbase” with the same capitalization.
Example: “pathbase” (will match), “PathBase” (will not match)
- 6. Prefix match (Case sensitive) : A prefix match will match any word that begins with “pathbase”, with the same capitalization.
Example: “pathbaseFolder” (will match), “pathbasedirectory” (will match), “PathBaseConfig” (will not match)
- 7. Suffix match (Case sensitive) : An exact match will only match the exact word “pathbase” with the same capitalization.
Example: “pathbase” (will match), “PathBase” (will not match)
- 8. Regex match (Case sensitive) : A regular expression can be used to match words that contain “pathbase”, with the same capitalization.
Example: bw*pathbasew*b This regular expression will match any word that contains “pathbase” as a separate word, with the same capitalization. For example: “pathbasefile” (will match), “mypathbaseProject” (will match), “dataPathBaseConfig” (will not match)
After added the Acl type Path Based and condition, you can see the list below.
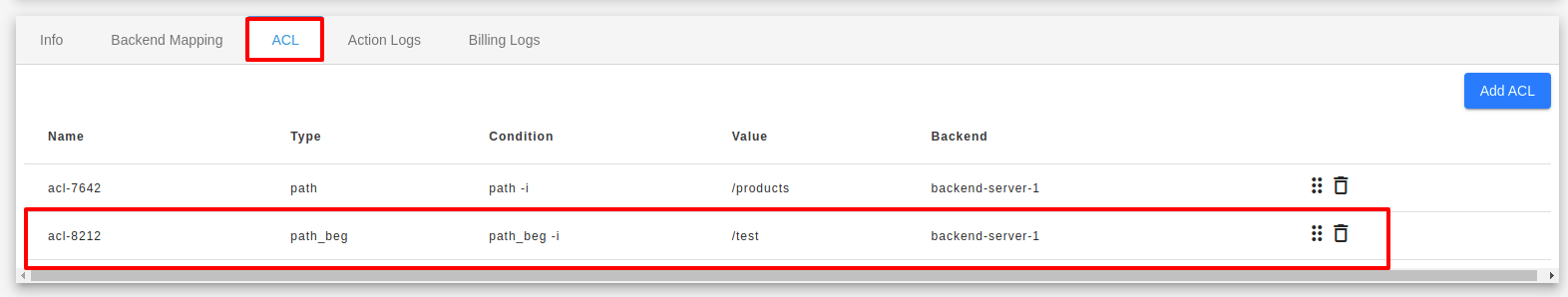
2. Host Based : - You can use host conditions to define rules that route requests based on the hostname in the host header known as host-based routing. For example, In below image, the host is added as test.e2enetworks.com
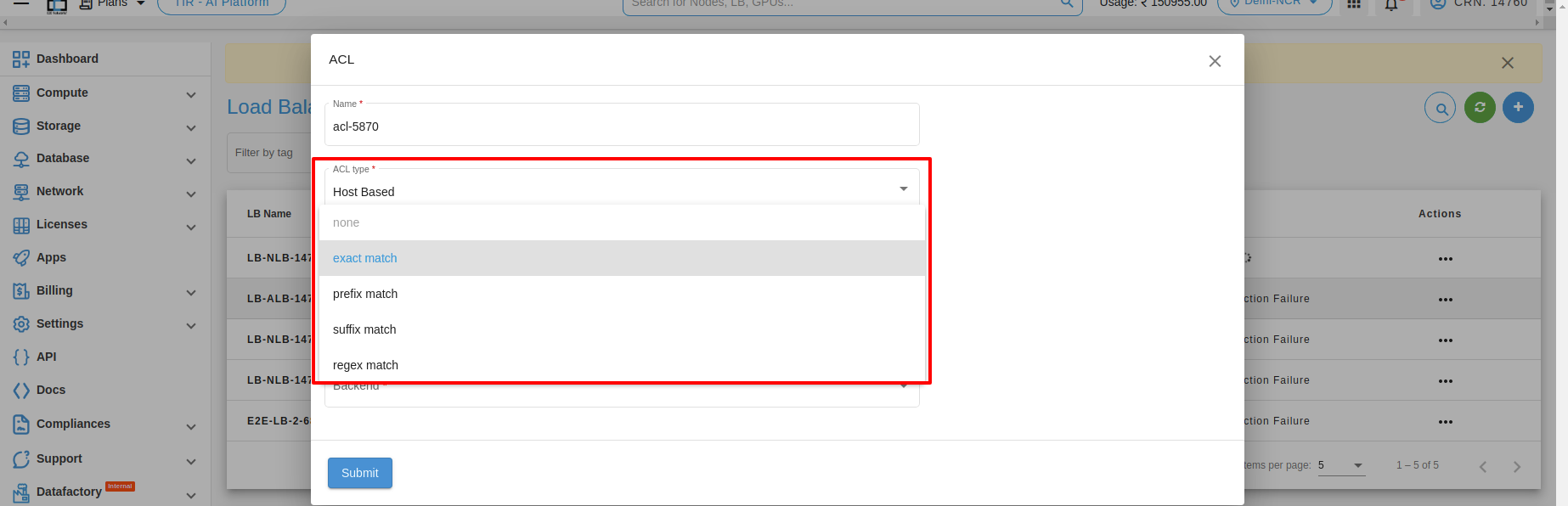
- 1. Exact Match : An exact match will only match the exact word “pathbase”.
Example: “pathbase”
- 2. Prefix matching: A prefix is a group of letters that appears at the beginning of a word. To perform prefix matching on “hostbase,” you would look for words that start with a certain set of letters.
- For example:
Prefix “host”: “hostname”, “hosting”, “hostile” Prefix “hos”: “hospital”, “hostess”, “hose”
3. Suffix matching: A suffix is a group of letters that appears at the end of a word. To perform suffix matching on “hostbase,” you would look for words that end with a certain set of letters.
- For example:
Suffix “base”: “database”, “homebase”, “knowledgebase” Suffix “host”: “ghost”, “hostess”, “host”
- 4. Regex match: A regular expression can be used to match words that contain “hostbase”.
- For example:
bw*pathbasew*b
Let’s break down this regular expression:
b matches a word boundary, which ensures that we only match “hostbase” as a separate word and not as part of another word.
w* matches zero or more word characters (letters, digits, or underscores).
hostbase matches the literal string “hostbase”.
w* matches zero or more word characters after “hostbase”.
b matches another word boundary to ensure that we have matched the complete word.
So this regular expression will match words like “hostbase”, “ghosthostbase”, “hostbase123”, “myhostbaseproject”, and so on.
After added the Acl type Host Based and condition, you can see the list below.

3. Query parameters Match : Query parameters are used in web development to pass data from a client to a server through the URL. Depending on the type of data you need to pass, you can use different types of query parameters, such as exact match, prefix match, suffix match, or regular expression (regex) match. Here are some examples of each:

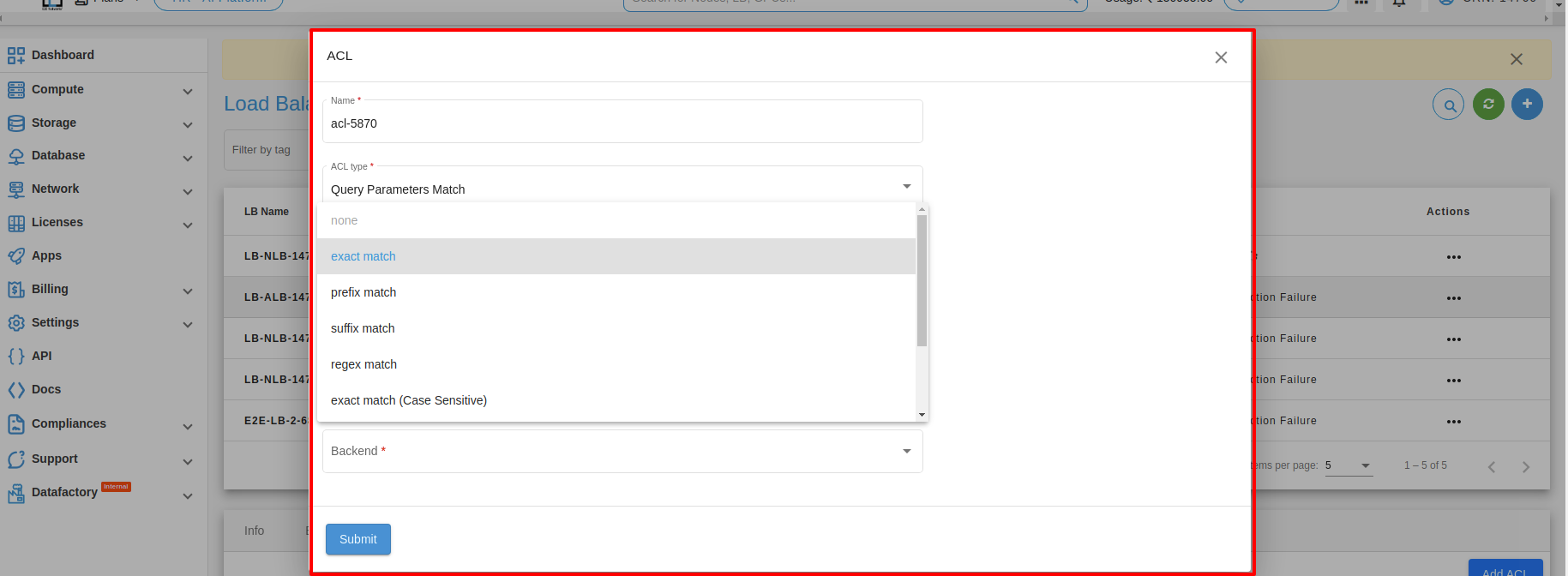
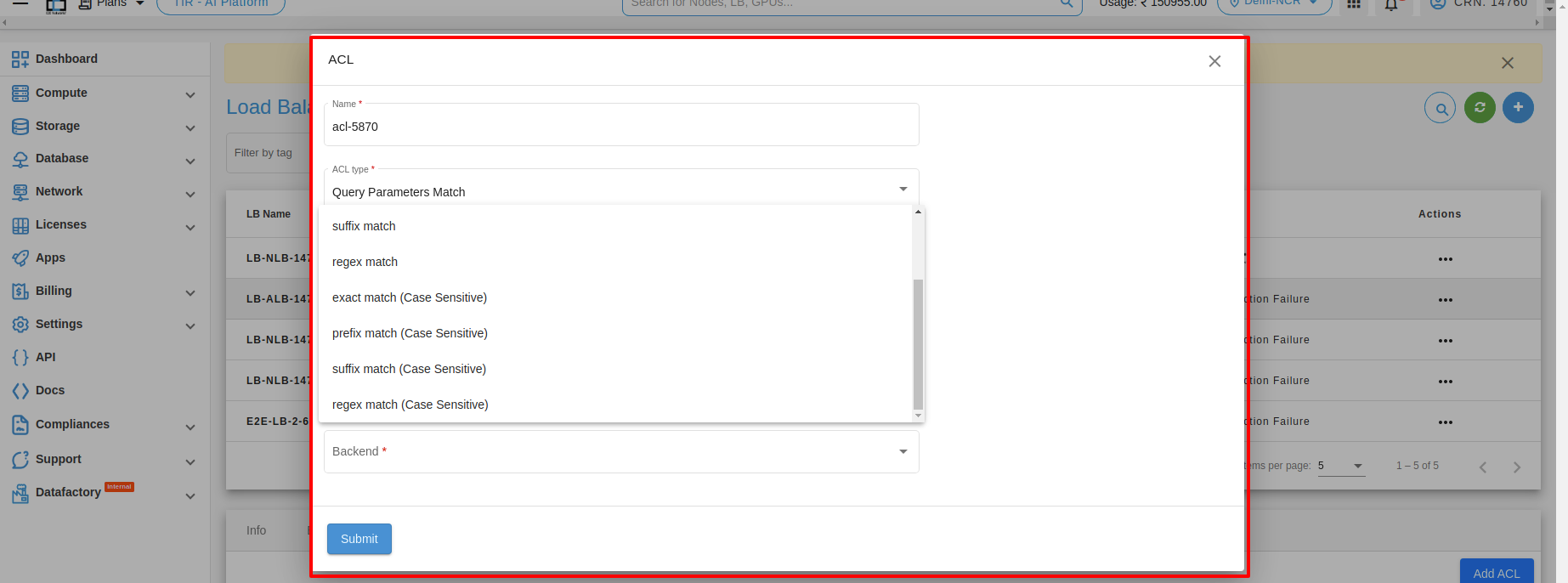
1. Exact match: This type of query parameter is used when you want to match a specific value exactly. For example, if you have a web application that displays information about different users, you could use an exact match query parameter to retrieve information about a specific user by their ID. Here’s an example URL:
https://example.com/users?id=123
In this case, the query parameter is “id=123”, which is an exact match for the user ID “123”.
2. Prefix match: This type of query parameter is used when you want to match values that start with a specific string. For example, if you have a search feature on your website that allows users to search for products by name, you could use a prefix match query parameter to retrieve all products that start with a specific string. Here’s an example URL:
https://example.com/search?query=phone
In this case, the query parameter is “query=phone”, which is a prefix match for any products that start with the string “phone”.
3. Suffix match: This type of query parameter is used when you want to match values that end with a specific string. For example, if you have a web application that displays information about different files, you could use a suffix match query parameter to retrieve all files that end with a specific file extension. Here’s an example URL:
https://example.com/files?type=pdf
In this case, the query parameter is “type=pdf”, which is a suffix match for any files that end with the “.pdf” file extension.
4. Regex match: This type of query parameter is used when you want to match values based on a complex pattern using regular expressions. For example, if you have a web application that searches for articles based on complex search criteria, you could use a regex match query parameter to retrieve articles that match a specific pattern. Here’s an example URL:
https://example.com/articles?search=python++programming
In this case, the query parameter is “search=python++programming”, which is a regex match for articles that contain the exact phrase “python++programming”. Note that the plus signs (+) are escaped with a backslash () to match them literally.
5. Exact match (Case-sensitive) : This type of query parameter is used when you want to match a specific value exactly, and you want the match to be case-sensitive. For example, if you have a web application that displays information about different users, and the user IDs are case-sensitive, you could use an exact match case-sensitive query parameter to retrieve information about a specific user by their ID. Here’s an example URL:
https://example.com/users?id=USER123
In this case, the query parameter is “id=USER123”, which is an exact match case-sensitive for the user ID “USER123”.
6. Prefix match (Case-sensitive) : This type of query parameter is used when you want to match values that start with a specific string, and you want the match to be case-sensitive. For example, if you have a search feature on your website that allows users to search for products by name, and the product names are case-sensitive, you could use a prefix match case-sensitive query parameter to retrieve all products that start with a specific string. Here’s an example URL:
https://example.com/search?query=phone
In this case, the query parameter is “query=phone”, which is a prefix match case-insensitive for any products that start with the string “phone”.
7. Suffix match (Case-sensitive) : This type of query parameter is used when you want to match values that end with a specific string, and you want the match to be case-sensitive. For example, if you have a web application that displays information about different files, and the file extensions are case-sensitive, you could use a suffix match case-sensitive query parameter to retrieve all files that end with a specific file extension. Here’s an example URL:
https://example.com/files?type=PDF
In this case, the query parameter is “type=PDF”, which is a suffix match case-sensitive for any files that end with the “.PDF” file extension.
8. Regex match (Case-sensitive) : This type of query parameter is used when you want to match values based on a complex pattern using regular expressions, and you want the match to be case-sensitive. For example, if you have a web application that searches for articles based on complex search criteria, and the search criteria are case-sensitive, you could use a regex match case-sensitive query parameter to retrieve articles that match a specific pattern. Here’s an example URL:
https://example.com/articles?search=Python++Programming
In this case, the query parameter is “search=Python++Programming”, which is a regex match case-sensitive for articles that contain the exact phrase “Python++Programming”. Note that the plus signs (+) are escaped with a backslash () to match them literally.
4. HTTP request method : HTTP request method matching is a feature commonly used in load balancers to direct incoming requests to specific servers or services based on the HTTP method used in the request. Here are some examples of how HTTP request method matching can be used in a load balancer:
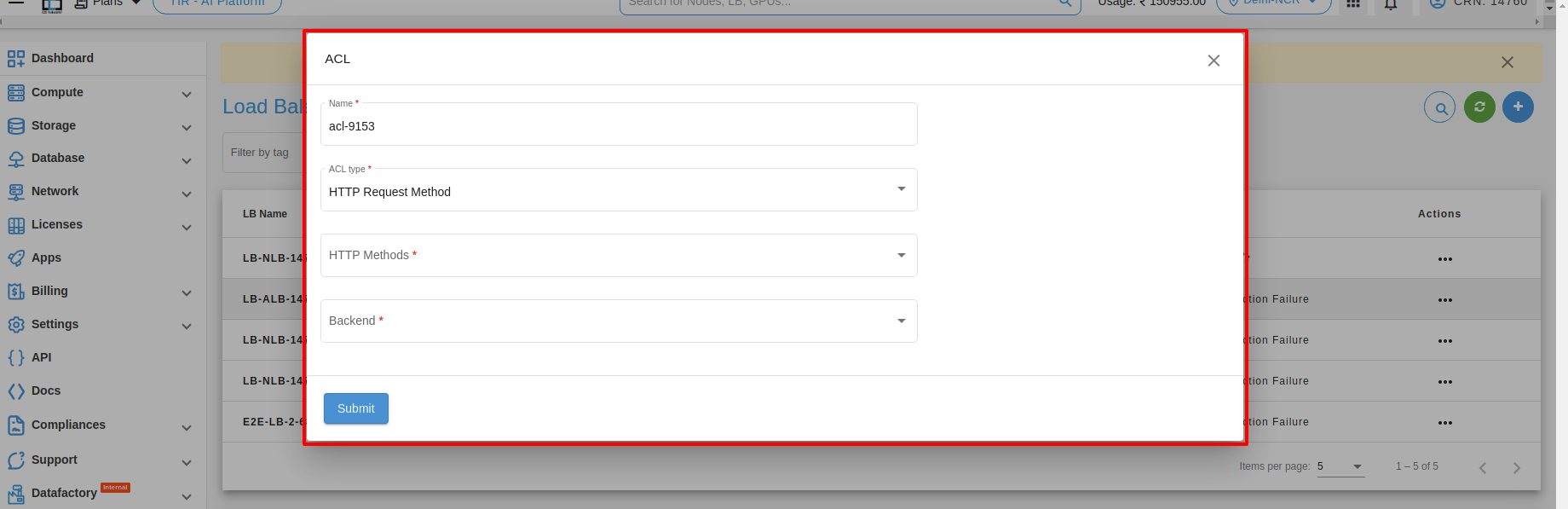
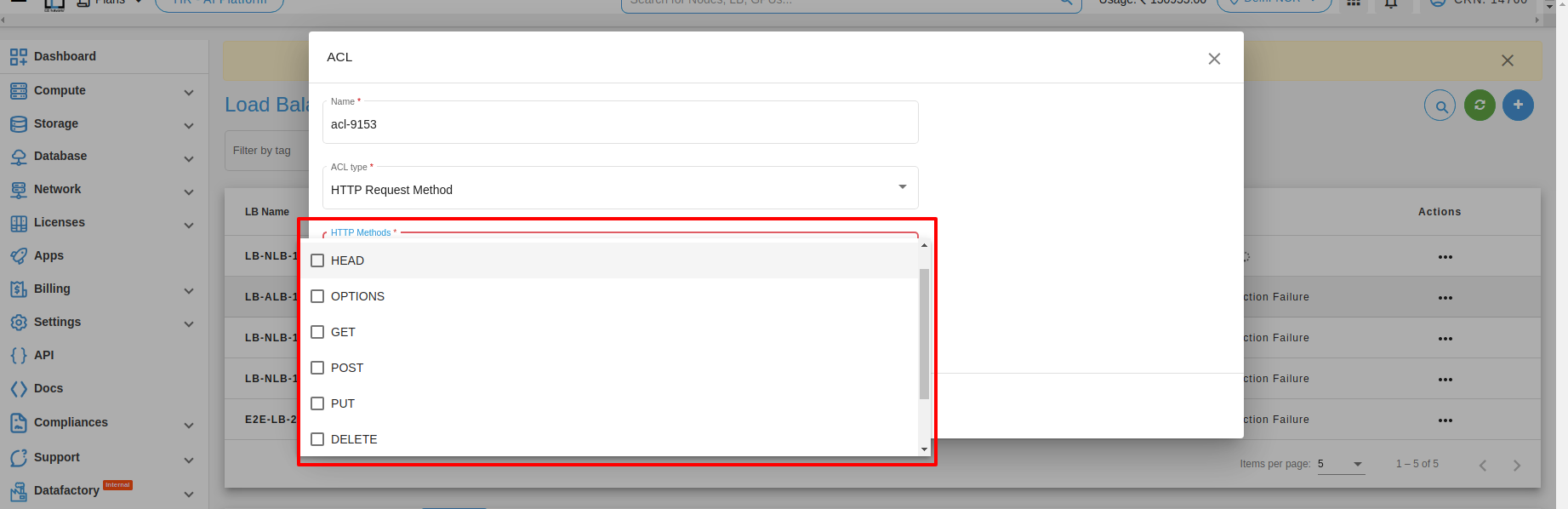
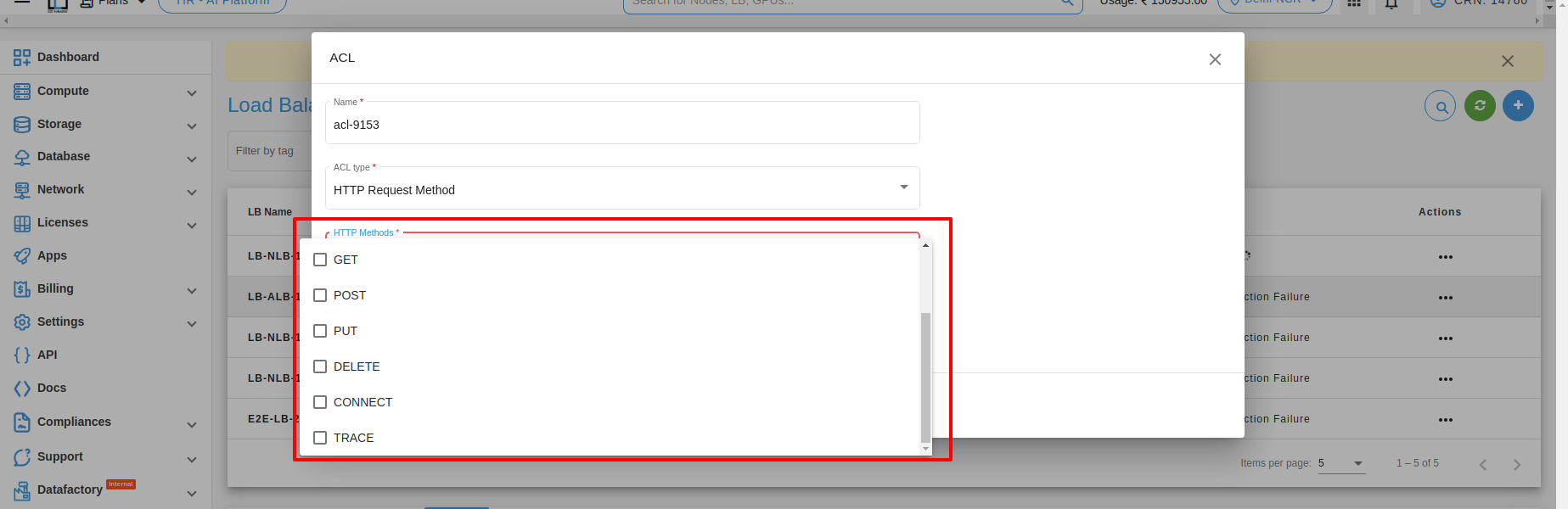
1. Match GET requests: This type of HTTP request method matching is used to direct all incoming GET requests to a specific server or service. For example, if you have a web application that serves static content from a dedicated server, you could use a load balancer to match all incoming GET requests and direct them to that server.
2. Match POST requests: This type of HTTP request method matching is used to direct all incoming POST requests to a specific server or service. For example, if you have a web application that handles form submissions on a dedicated server, you could use a load balancer to match all incoming POST requests and direct them to that server. http-request allow if { method POST }
3. Match PUT requests: This type of HTTP request method matching is used to direct all incoming PUT requests to a specific server or service. For example, if you have a web application that handles file uploads on a dedicated server, you could use a load balancer to match all incoming PUT requests and direct them to that server. Here’s an example configuration in the load balancer:
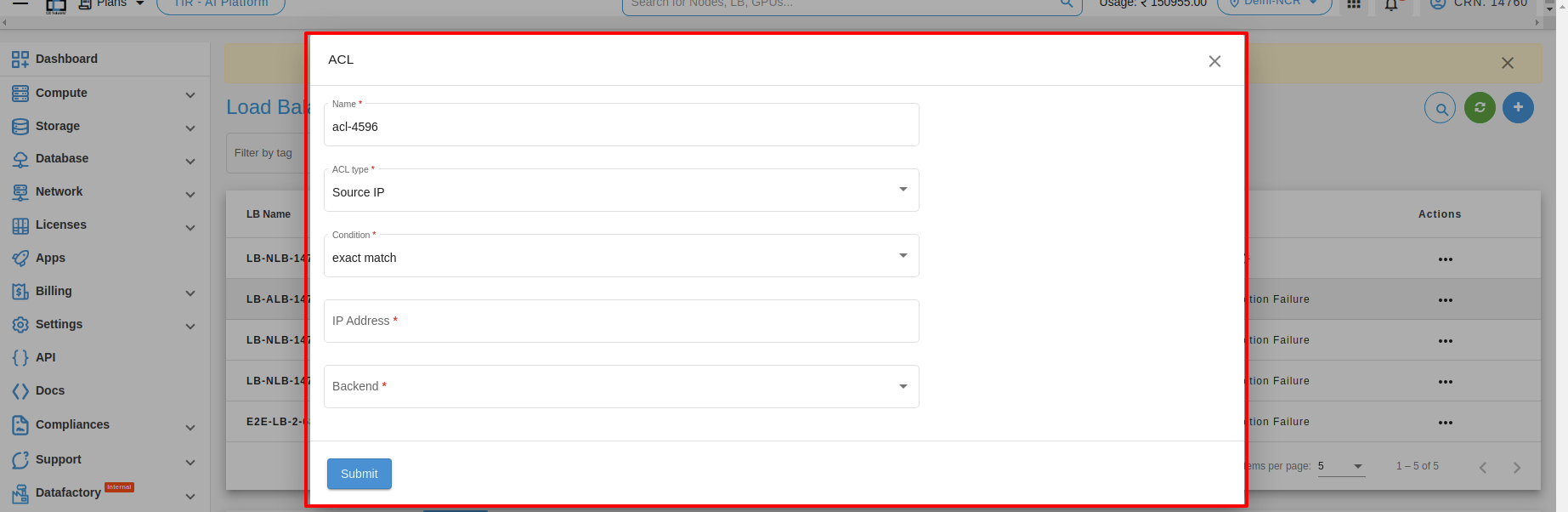
4. Source IP : Source IP matching is a feature commonly used in load balancers to direct incoming requests to specific servers or services based on the source IP address of the request. Here’s an example of how source IP matching can be used in a load balancer.
Match requests from a specific IP address: This type of source IP matching is used to direct all incoming requests from a specific IP address to a specific server or service. For example, if you have a client that is accessing your application from a dedicated IP address, you could use a load balancer to match all incoming requests from that IP address and direct them to a specific server.
Match requests from a range of IP addresses: This type of source IP matching is used to direct all incoming requests from a range of IP addresses to a specific server or service. For example, if you have a set of servers that are optimized for handling requests from a specific geographic region, you could use a load balancer to match all incoming requests from that region and direct them to those servers. Here’s an example configuration in the load balancer:
Monitoring
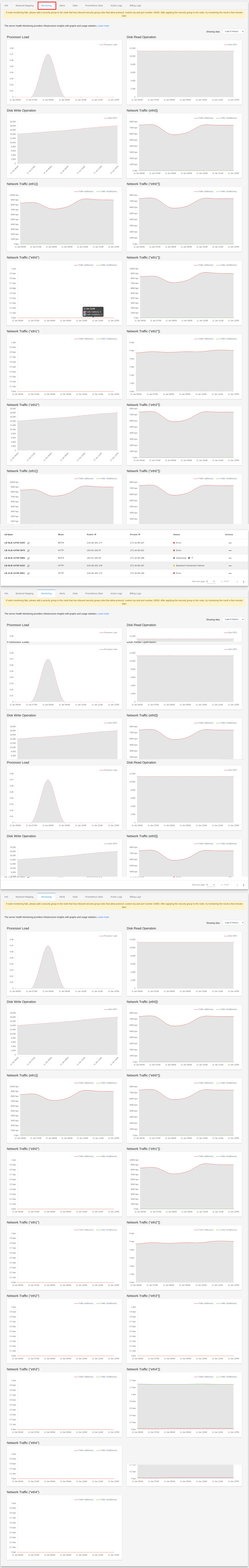
Monitoring is an important part of maintaining the reliability, availability, and performance of your load balancer . You can check the monitoring information for your load balancer on the Monitoring tab. This information is collected from your load balancer and processes raw data into readable graphs. Each graph is based on one of the different metrics. Learn more.
Alerts
Server health alerts are default created for your newly created load balancer using recommended parameters for alert policy. Also, you can set up new alerts by defining trigger parameters as per your use case. The alerting system works by sending automatic response notifications to your defined email list. Learn more
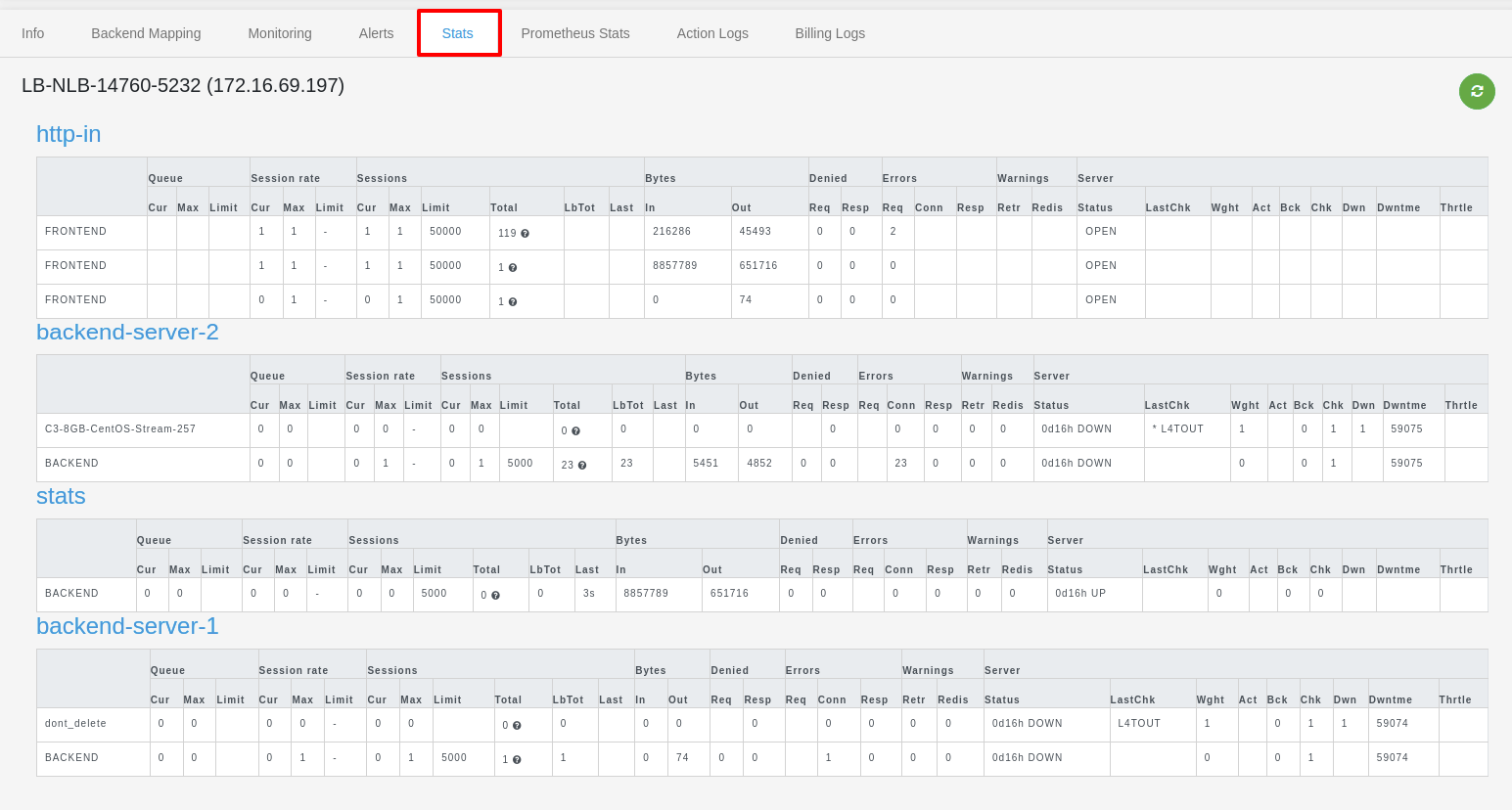
Stats
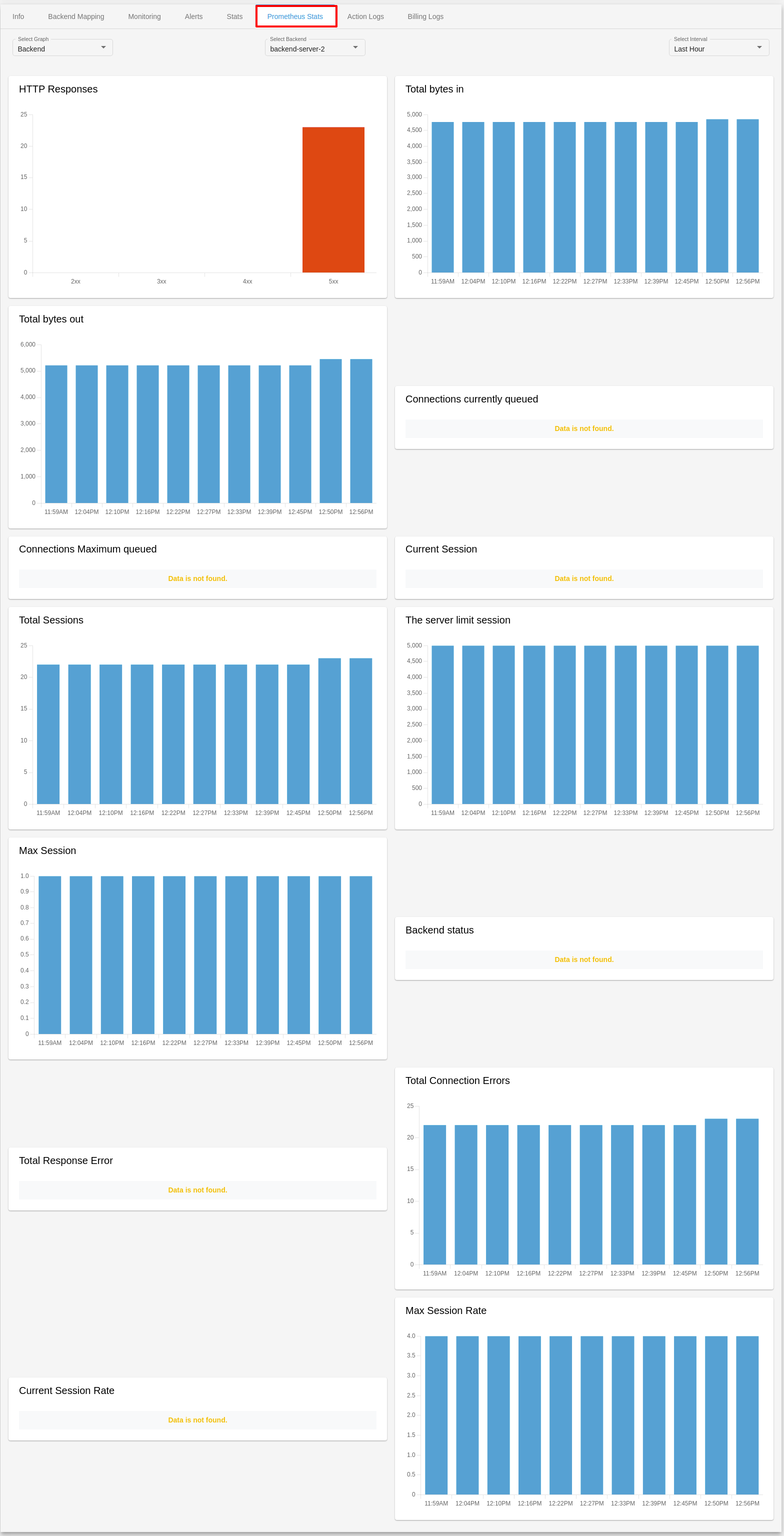
Prometheus Stats
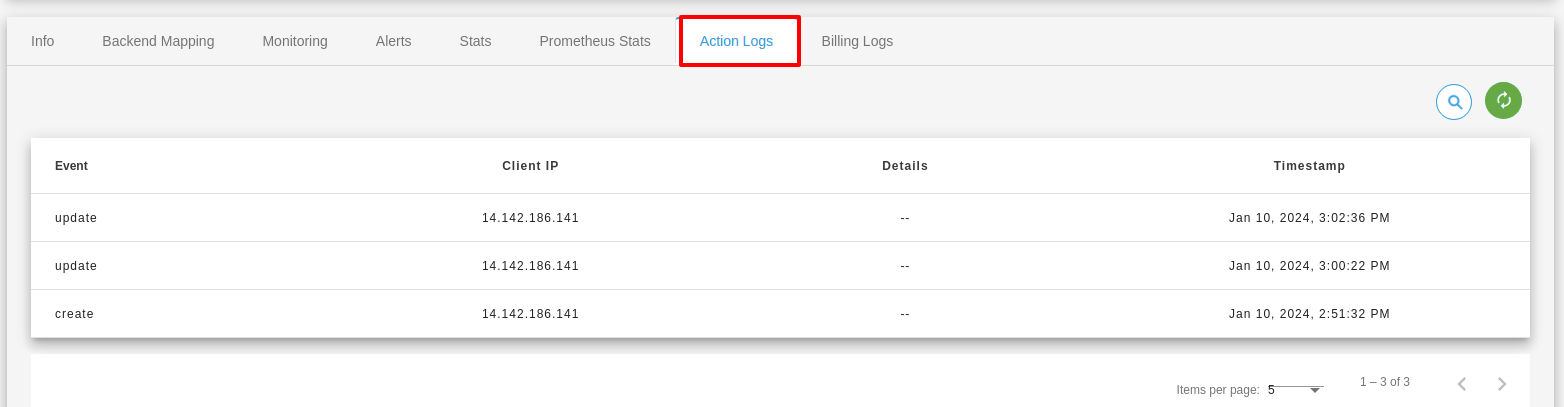
Action Logs
Action logs contain detailed information about requests sent to your load balancer such as the date/time the request was received, client’s IP address, request protocol, request paths, and server responses. These access logs are useful to application incoming network traffic patterns and troubleshoot issues if any arise.
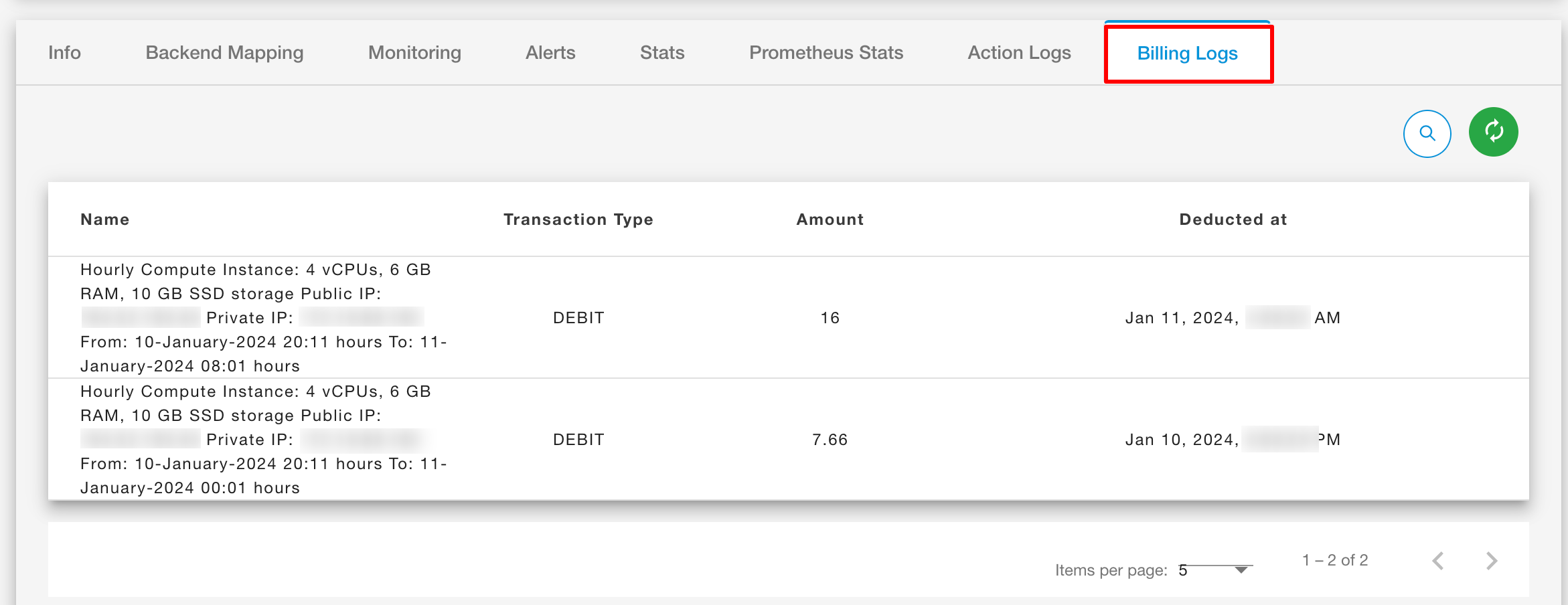
Billing Logs
Actions
Types of action which you can perform with Load Balancer.
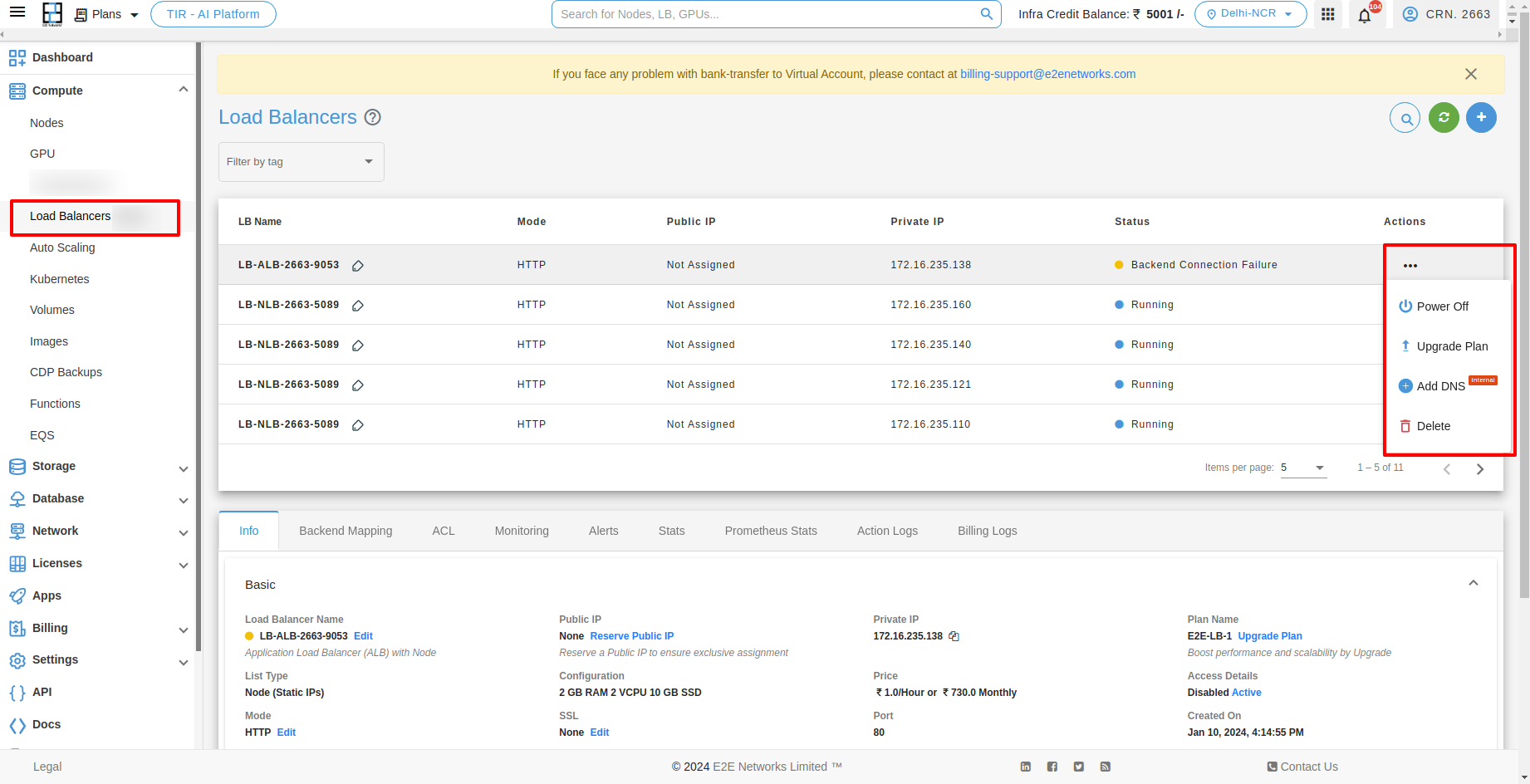
Stopping your Load Balancer
If you want to stop Load Balancer then you have to click on Stop button. And after clicking on that the confirmation popup will be open and you have to click on Power Off button.
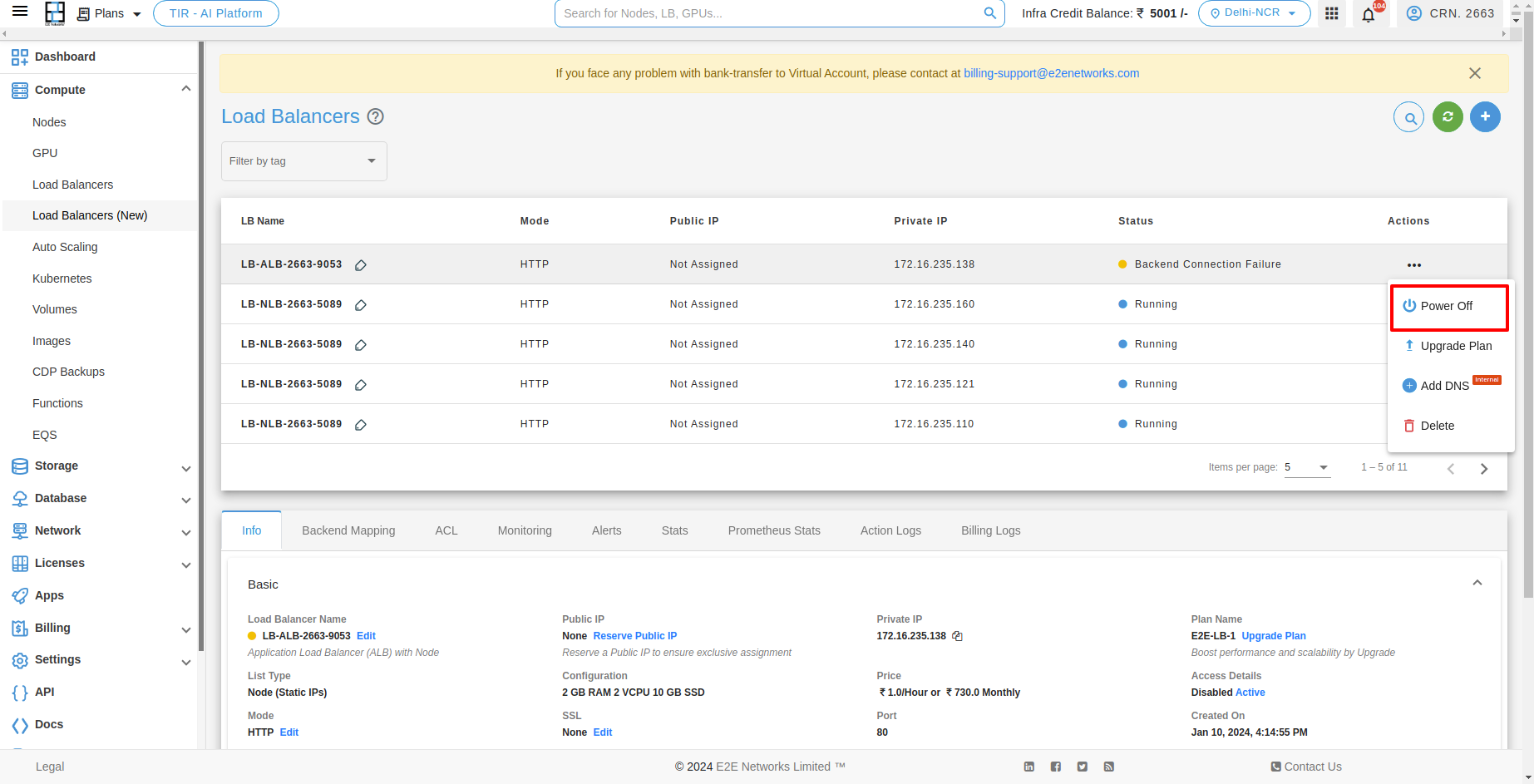
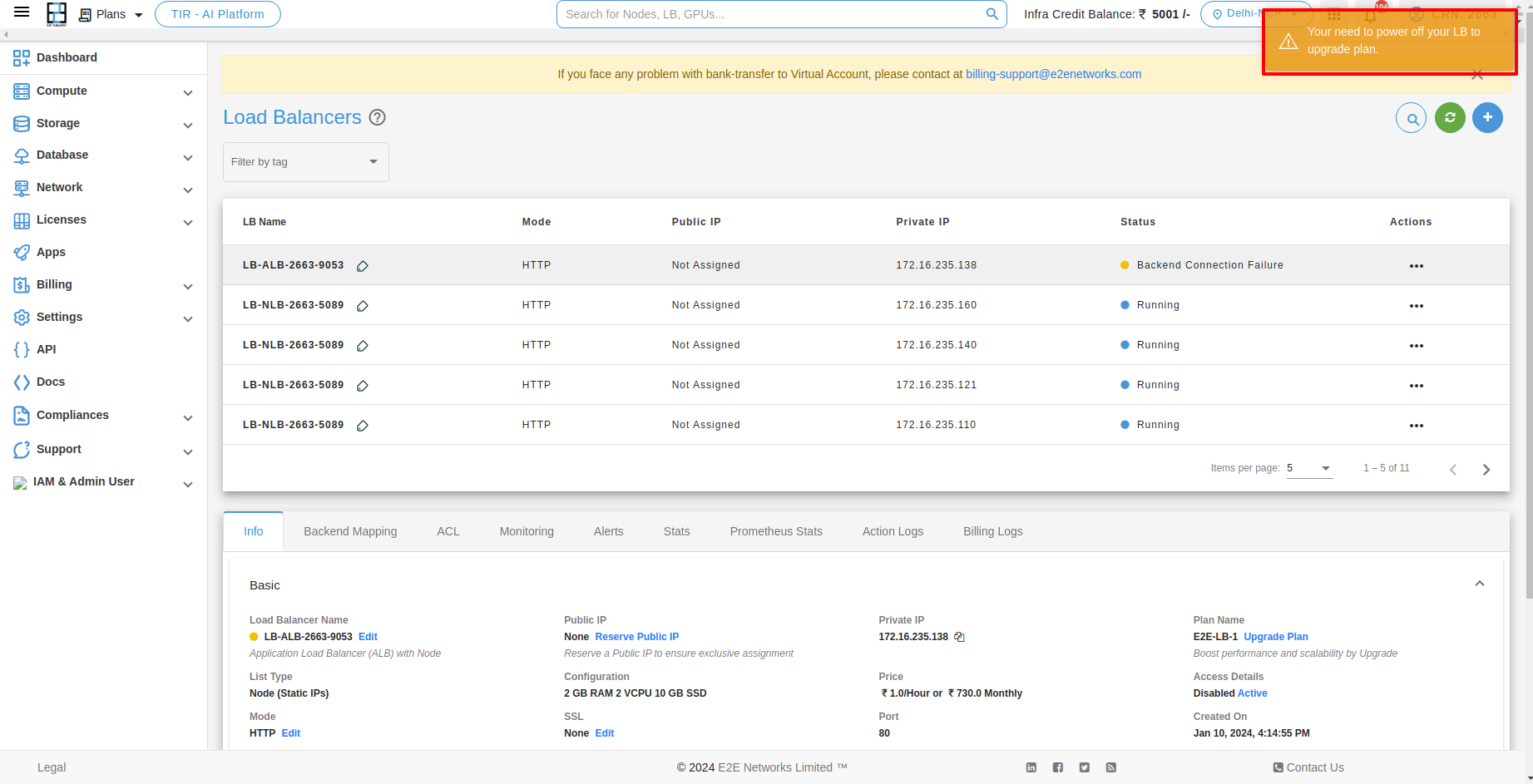
Upgrade your Load Balancer
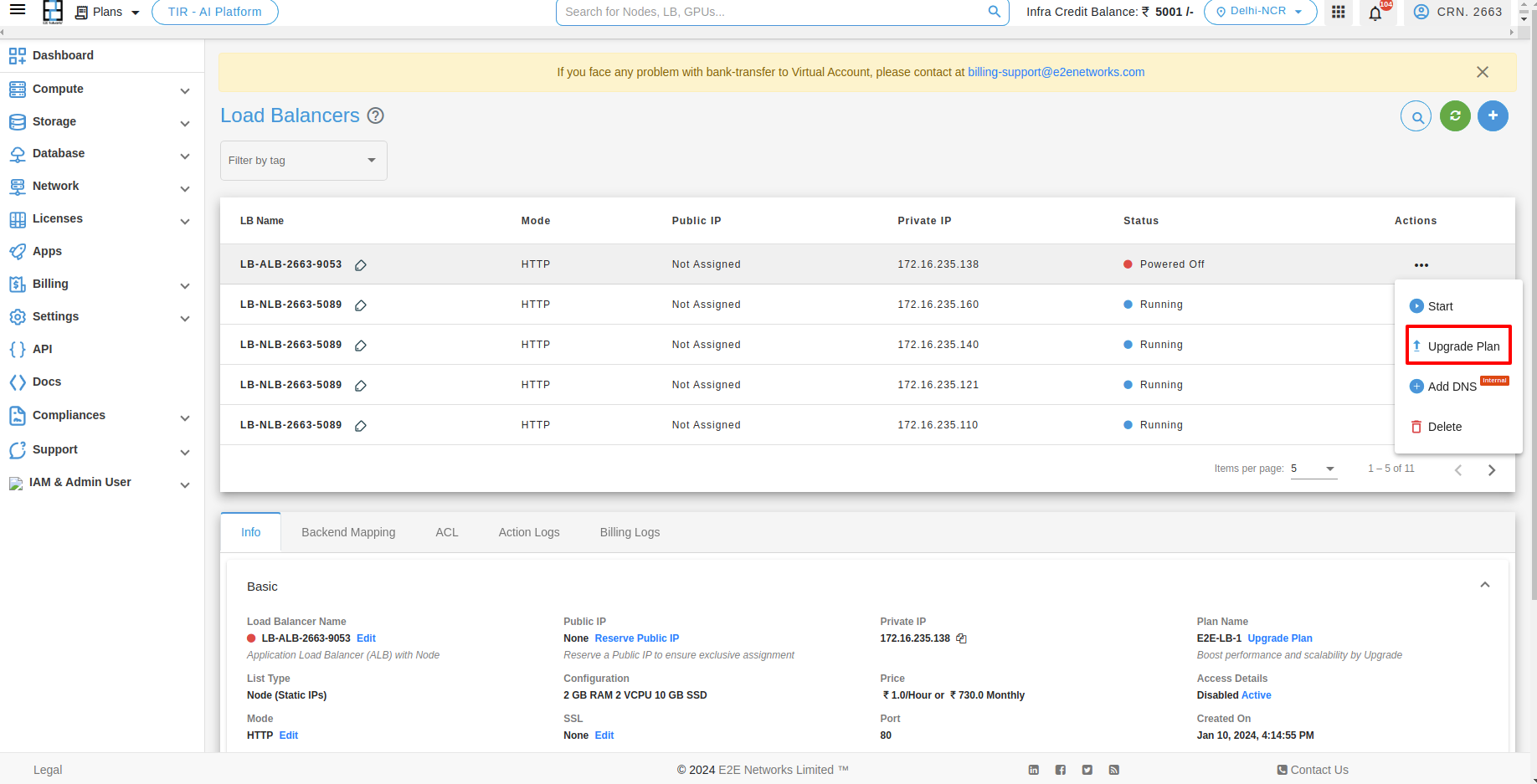
The LB upgrade feature enables customers to easily upgrade their LB plan based on their specific usage requirements. For upgrading your Load Balancer you have to click on Upgrade button under Action button.
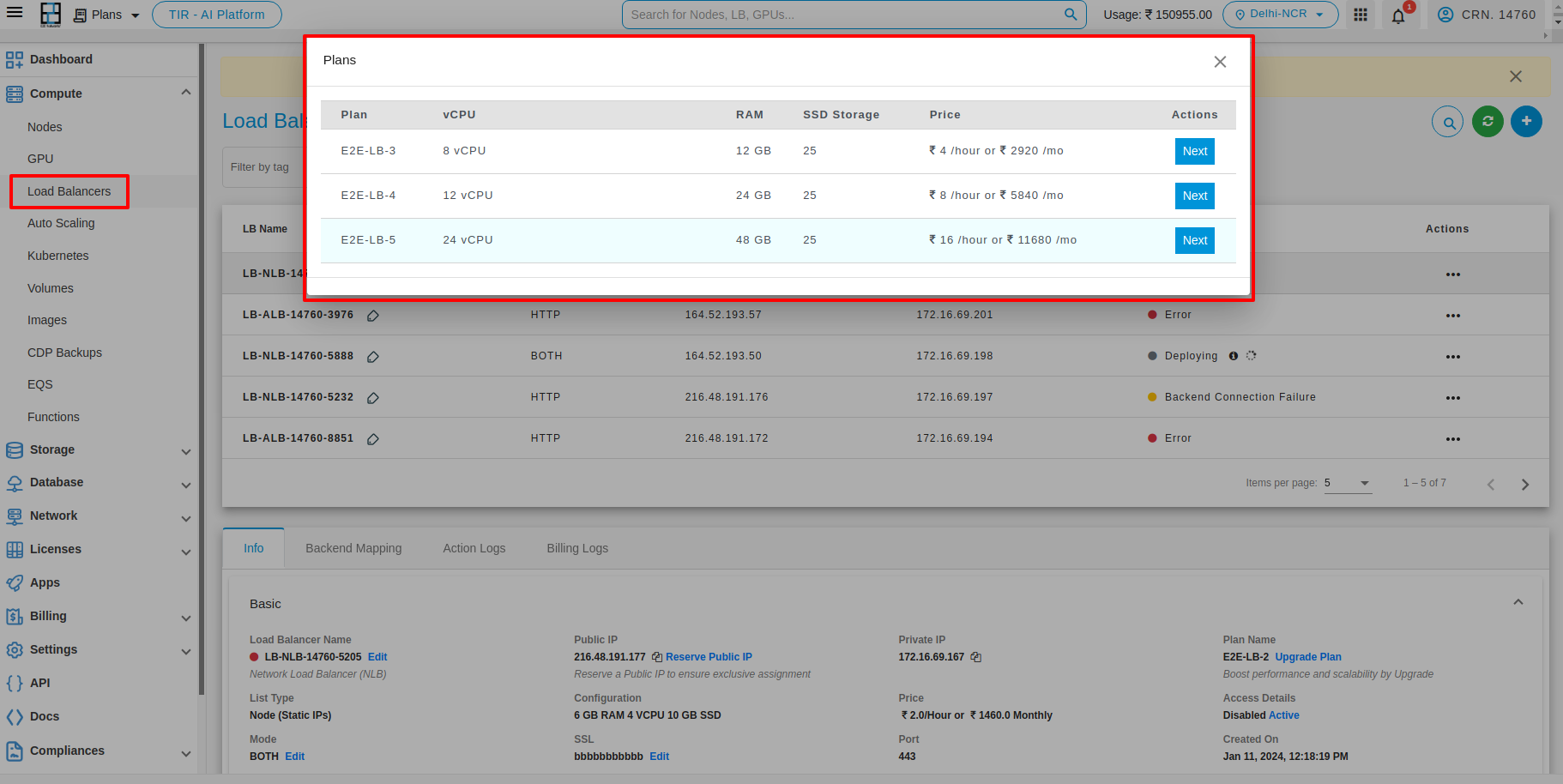
After that you have to click on Apply button with the selected plan. Then the upgrading process will be start.
Note
Please ensure that your load balancer is stopped when performing the upgrade action.
Delete
For Deleting your Load Balancer you have to click on Delete button.